Hunting Insecure Direct Object References (IDORs)
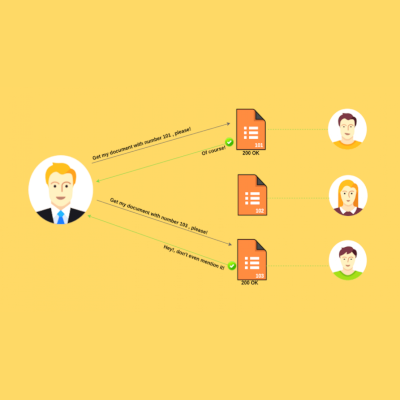
HUNTING INSECURE DIRECT OBJECT REFENCES (IDORs) This blog post was written by Rodney Kariuki. Introduction Insecure Direct Object Reference (IDOR) is a type of access control vulnerability that arises when the references to data objects (like a file or a database entry) are predictable, and the application uses user-supplied input [...]