BLOG POSTS
Capturing NetNTLM V2 hashes Via Outlook Signatures
CAPTURING NET-NTLM V2 HASHES VIA OUTLOOK SIGNATURES [...]
Persistence: Common Userland Techniques (Part 2)
PERSISTENCE: COMMON USERLAND TECHNIQUES (PART 2) [...]
Persistence: Common Userland Techniques (Part 1)
PERSISTENCE: COMMON USERLAND TECHNIQUES (PART 1) [...]
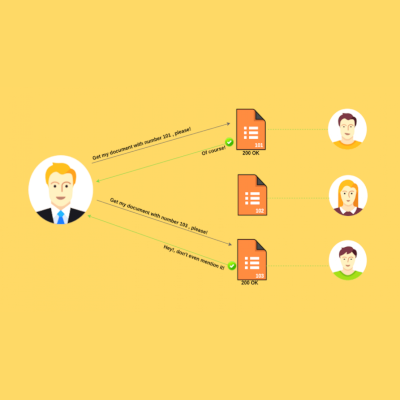
Hunting Insecure Direct Object References (IDORs)
HUNTING INSECURE DIRECT OBJECT REFENCES (IDORs) [...]
Windows Privilege Escalation
WINDOWS PRIVILEGE ESCALATION This blog post [...]
Initial Access With Maldocs – A TTP Story
INITIAL ACCESS WITH MALDOCS [...]