DNS TUNNELING FOR DEFENCE EVASION AND COMMAND AND CONTROL

This blog post was written by Alex Maina.
Introduction
Before we look at exploiting DNS through DNS tunneling we need to understand DNS and how it is critical to an organization’s infrastructure.
DNS is used to translate IP addresses into domain names.
For example, if you type the URL, www.example.com in your browser it is the DNS that is responsible for converting the domain name to the relevant IP then displaying the content of the URL in the browser.
More on DNS can be found here:
Why is this Important:
The most notable ones are:
- DNS is the only system that can help you browse the internet. Without DNS then the internet as we know it would not exist.
- No need to memorize IP addresses – as DNS servers provide a solution for converting domain or subdomains to IP addresses.
This is very important for most organizations.
Hackers (blackhats) can also exploit DNS for malicious purposes as listed below as some of the disadvantages of DNS.
Disadvantages
- DNS queries don’t carry any information about the client who initiated it, this is very useful for blackhats as the server side will only see the IP address from where the query came from.
- Another disadvantage is the way DNS servers are built an example is if the main server is broken or altered it will be hard to access the page that was hosted on the server (blackhats) can use this to their advantage by targeting the main servers of popular websites to redirect to users to malicious sites e.g. the watering-hole technique which has been used by several APTs as seen below to target popular websites.
More on this can be found here:
Drive-by Compromise, Technique T1189 – Enterprise | MITRE ATT&CK®
Another method that an attacker can use is DNS to his advantage is through DNS tunneling for command and control, defense evasion and data exfiltration as it is not a highly monitored protocol by firewalls and disabling it could hinder usage of the internet
DNS Tunneling
DNS tunneling is a nonstandard solution to exchange data using the DNS protocol.
There are different types of DNS Tunneling:
- HTTP-DNS tunneling
- HTTPS-DNS tunneling
- POP3-DNS tunneling
- FTP-DNS tunneling
This can be used maliciously to establish, Command and control channels with an external server or Data Exfiltration./p>
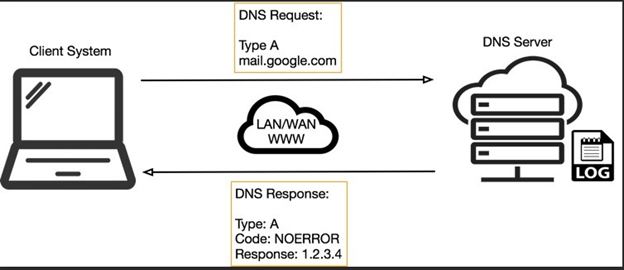
From the image above we can see a simple representation of a DNS tunnel between a client and server.
Demo of how DNS can be used to establish command and control:
For this, we will be using Blackarch a penetration testing distro based on Arch Linux as the attacker machine and windows system as the target machine.
The tool we will be using is DNSCAT2 by Ron or iagox86 a Proof of Concept (POC) tool for the above attack.
DNSCAT2 Installation
You will require GoLang to be installed for this. It can be installed using the commands below:
git clone https://github.com/iagox86/dnscat2.git
cd dnscat2/server/
gem install bundler
bundle install
To start the server use the following command:
sudo ruby dnscat.rb –dns “domain=hacker,host=192.168.0.28” –no-cache
Demo Videos are below:
Command and Control using DNSCAT2:
As you can see from the video above we were able to establish a command and control channel through DNS while an updated version of windows defender was running.
TODO
Now to demonstrate this in a phishing attack we can use hot-manchego by fortyNorthSecurity to create a Maldoc to execute the DNSCAT2 PowerShell client.
Then we can try and employ the red team concept of Bring Your Own Land (BYOL) on the compromised machine by running BITSAdmin to download our malware and enumeration tools.
Detecting and Mitigation of DNS Tunneling
- Looking at the frequency of DNS requests – For example if the number of DNS requests from a host are usually 100/200 then suddenly the number spikes up to 500/600 request this could indicate that dns tunneling it be employed on the host network.
- Length of a DNS request – The typical length of a DNS request is not that long e.g. that of google.com. If blue teams notice a longer DNS request this could imply that DNS tunneling is in place and they could use third-party software to create an alert when this happens.
- Destination of the DNS requests, most companies have their own DNS servers which clients use for the DNS resolution. Through the use of third-party software, we could detect external DNS Servers and create an alarm if there are any outbound DNS connections.
- The pattern of the DNS requests. For example, a typical URL will not consist of a lot of number’s but when DNS tunneling is employed by the attacker the data could consist of a lot of numbers as it is encoded. This could suggest the use of DNS tunneling. Through third-party software’s we could create rules to detect this and alert blue teams. A good example of this third party software’s include:
-
- Norton
- LogRhythm
You can also refer to the following blog for more information:
Detecting DNS Tunneling | LogRhythm
Application in the Real World
As you can see abusing DNS has been employed by a lot of APTs for different purposes as per MITRE ATT&CK. The main reason being it is not a heavily monitored protocol.
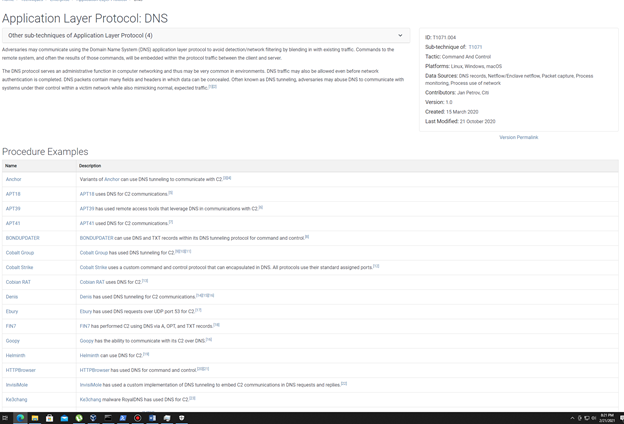
More on this can be found here:
Application Layer Protocol: DNS, Sub-technique T1071.004 – Enterprise | MITRE ATT&CK®
One major disadvantage of using this protocol is that it is quite slow as compared to using protocols such as HTTP and HTTPS.
Disclaimer
The MacroSec blogs are solely for informational and educational purposes. Any actions and or activities related to the material contained within this website are solely your responsibility. The misuse of the information on this website can result in criminal charges brought against the persons in question. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.

![The Auror Project – Challenge 1 [Setting the lab up automatically]](https://macrosec.tech/wp-content/uploads/2022/04/Auror-Project-500x383.png)


