PDF CRACKING WITH CLOUD COMPUTING

This blog post was written by Varun Gupta.
Introduction
Hashcat is a popular password cracker and designed to break even the most complex password representation. To do this, it enables the cracking of a specific password in multiple ways, combined with versatility and speed.
Password representations are primarily associated with hash keys, such as MD5, SHA, WHIRLPOOL, RipeMD, NTMLv1, NTMLv2, and so on. They are also defined as a one-way function — this is a mathematical operation that is easy to perform but very difficult to reverse engineer.
However, it takes really long to crack some of the passwords, and it hugely depends on the computing resources. Therefore, to make the process faster, we can use Cloud Computing to crack passwords to make the process more efficient. To achieve this, Colabcat comes to the rescue.
What is Colabcat?
Colabcat project runs Hashcat on Google Colab with session restore capabilities with Google Drive.
Colabcat creates a symbolic link between the dothashcat folder in your Google Drive and the /root/.hashcat folder on the Google Colab session.
This enables seamless session restore even if your Google Colab gets disconnected or you hit the time limit for a single session by syncing the .restore, .log, and the .potfile files across Google Colab sessions by storing them in your Google Drive.
What is Google Colab?
Google Colab is a Python development environment that runs in the browser using Google Cloud.
Google Colab allows you to write and execute Python in your browser, with:
- Zero Configuration Required
- Free access to GPUs
- Easy Sharing
The following video explains it in more detail:
https://www.youtube.com/watch?v=inN8seMm7UI
Password cracking is mapped to T1110.002 – Brute Force: Password Cracking in the MITRE ATT&CK Framework.
It is a sub-technique of T1110 – Brute Force in the MITRE ATT&CK Framework.
Use Case Scenario
We are on a Penetration Testing engagement, and we have managed to exfiltrate a particular PDF file that looks interesting.
However, the file is password-protected, and we need to crack the password to read the contents of the file.
We will use Colabcat to brute force the password of the PDF file.
Setting Up Colabcat
The video below demonstrates how to do the initial setup of Colabcat:
Cracking the PDF Password
After Colabcat is set up, let us look at the pdf file whose password we want to crack. In the example, I will be using the certificate.pdf file. First, we need to extract the hash of the pdf file. This can be done by using pdf2john, which comes inbuilt in Kali Linux installations. If you do not have pdf2john, you can easily get it after installing John The Ripper tool from Github. To locate pdf2john, we will type the following commands:
updatedb
locate pdf2john
After we have located pdf2john, we will use it to extract the hash from our pdf file by using the commands:
/usr/share/john/pdf2john.pl certificate.pdf
After running the command, we will get a hash. However, hashcat just needs the hash after the file name and the colon symbol. So, we need to copy the hash after the colon and save it in a .txt file. In my case, I will be saving it in the pdfhash.txt file.
After doing so, we need to get the properties of the pdf file and which version it is using. This will be helpful to us while we are trying to crack the hash. To get the file properties, type the command:
file certificate.pdf
The screenshot for the above commands and output is below:
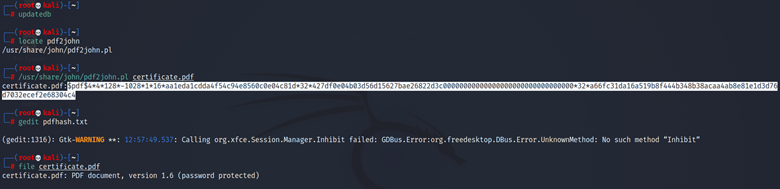
As it can be seen, the version is 1.6, and it also shows that the PDF is password protected. Also, note that the highlighted hash in white is what is saved in the pdfhash.txt file.
After getting the pdf hash, we need to upload the file to our hashes directory of Google Drive, which we had created earlier. After uploading the file, we should have two files in the hashes directory as shown below:
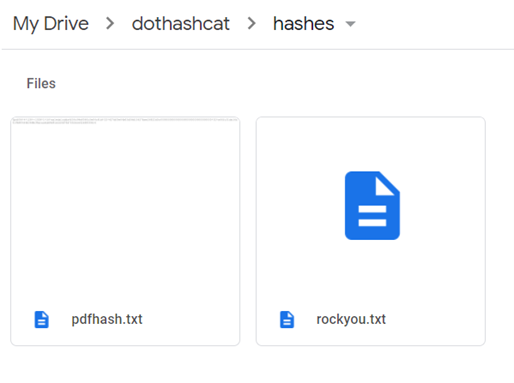
We can also check that both the files are uploaded successfully by going to Colabcat and typing the command:
!ls /root/.hashcat/hashes

After the files are uploaded, now we need to crack the hash. First, we need to figure out which hash mode to use. To do this, you can display the help menu of hashcat by typing:
hashcat -h
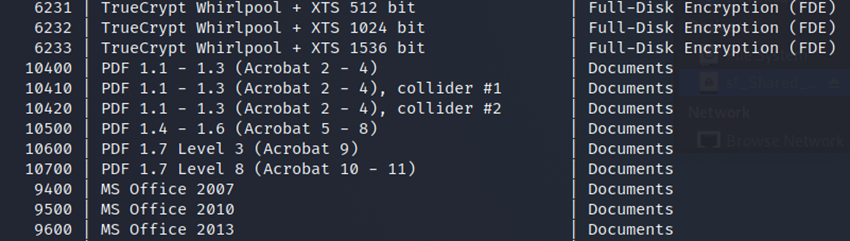
As it can be seen, the hash mode used for PDF Version 1.6 (gotten earlier) is 10500. After having this information, we can finally type the command to crack the PDF Password. We will be using rockyou.txt to crack the PDF Password.
To do so, go to Colabcat, and type the command below:
!hashcat -m 10500 -a 0 /root/.hashcat/hashes/pdfhash.txt /root/.hashcat/hashes/rockyou.txt
-m specifies the hash mode to be used. -a specifies the attack mode to be used, which is the Straight attack mode in our case. After that, the pdfhash.txt is passed as an input, and the rockyou.txt is passed as the wordlist.
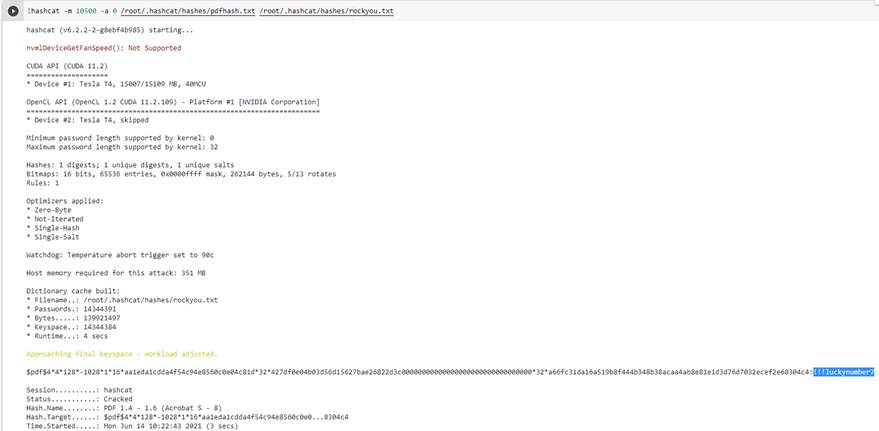
As it can be seen, the password is cracked within 3 seconds, and “!!!luckynumber7” is our password. This password can now be put while opening the PDF File to gain access to the contents of the PDF File.
The attack is very fast as compared to using hashcat on my own laptop. To give some context, if I used the OneRuleToRuleThemAll rule file to crack the same hash, the time estimated to crack the hash on my own laptop showed around 14 days and 10 hours. However, when I used the same rule file to crack the hash using Colabcat, the estimated time was 18 hours and 35 minutes. This should make it crystal clear as to why it is much more beneficial to use Colabcat as compared to using Hashcat on your host machine.
Prevention
There is hardly any detection or prevention mechanism for this type of attack as the password is cracked offline. The most effective prevention mechanism would be to create a strong password of a minimum of 8 characters and following password complexity.
References
https://github.com/someshkar/colabcat
Disclaimer
The MacroSec blogs are solely for informational and educational purposes. Any actions and or activities related to the material contained within this website are solely your responsibility. The misuse of the information on this website can result in criminal charges brought against the persons in question. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.

![The Auror Project – Challenge 1 [Setting the lab up automatically]](https://macrosec.tech/wp-content/uploads/2022/04/Auror-Project-500x383.png)


