USING ELASTALERT TO ALERT VIA EMAIL WHEN MIMIKATZ IS RUN.

This blog post was written by Dharmik Karania
Introduction
In this blog, I shall discuss how an alert can be sent via email when Mimikatz is run.
Mimikatz is a post-exploitation tool that is used to dump passwords from memory, along with hashes. This allows attackers to conduct various other attacks such as lateral movement more easily. When an attacker gains an initial foothold to a machine, they may run Mimikatz in order to retrieve passwords or passwords hashes. As blue teamers, it is crucial to setup mechanisms to detect attacks and take appropriate measures to safeguard information systems.
Prerequisites:
- ELK Setup
- Configure winlogbeat on Windows Machine
Introduction to ELK
According to Elastic, “ELK” is the acronym for three open-source projects: Elasticsearch, Logstash, and Kibana. Elasticsearch is a search and analytics engine. Logstash is a server side data processing pipeline that ingests data from multiple sources simultaneously, transforms it, and then sends it to a “stash” like Elasticsearch. Kibana lets users visualize data with charts and graphs in Elasticsearch.
To setup ELK, you can either use the GitHub repository or setup manually. I have setup my stack manually. Once the ELK stack has been installed successfully, the next step is to install Elastalert.
To install and setup Elastalert, I shall run the following commands on the terminal window.
sudo apt-get install -y python
sudo apt-get install -y python-pip python-dev libffi-dev libssl-dev
git clone https://github.com/Yelp/elastalert.git
cd elastalert
sudo pip install “setuptools>=11.3”
sudo pip install pyOpenSSL
sudo python setup.py install
sudo pip install “elasticsearch>=5.0.0”
cp config.example.yaml config.yaml
The config.yaml file needs to be edited in order to update the es_host with the IP address of the elasticsearch server.
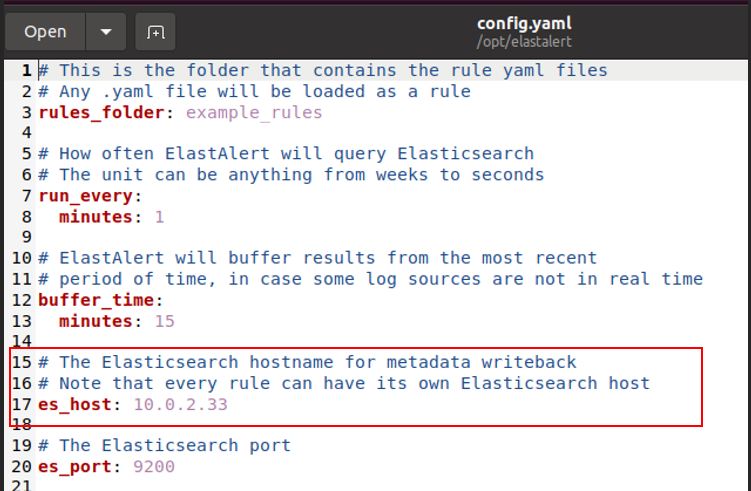
The next step is to create the Elastalert index by typing the command:
elastalert-create-index
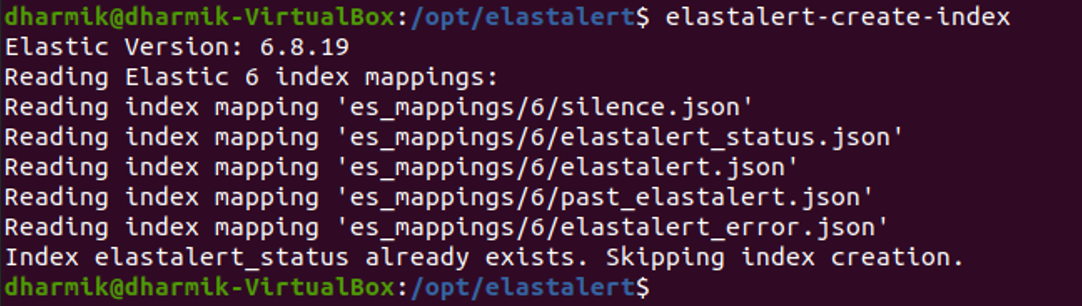
Configuring Postfix Gmail SMTP.
To be able to receive alerts on Gmail, there are some configurations I will need to do on my ELK Server. First off, I will need to install Postfix and its dependencies by running the following command:
sudo apt-get install postfix mailutils libsasl2-2 ca-certificates libsasl2-modules
Once the installation is complete, we need to edit the main.cf file. The file is found at this location:
/etc/postfix/main.cf
In the main.cf file, find the line which indicates inet_protocols and change it to ipv4.
Also add the following lines of code in the file as shown below:
relayhost = [smtp.gmail.com]:587
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd
smtp_sasl_security_options = noanonymous
smtp_tls_CApath = /etc/ssl/certs
smtpd_tls_CApath = /etc/ssl/certs
smtp_use_tls = yes
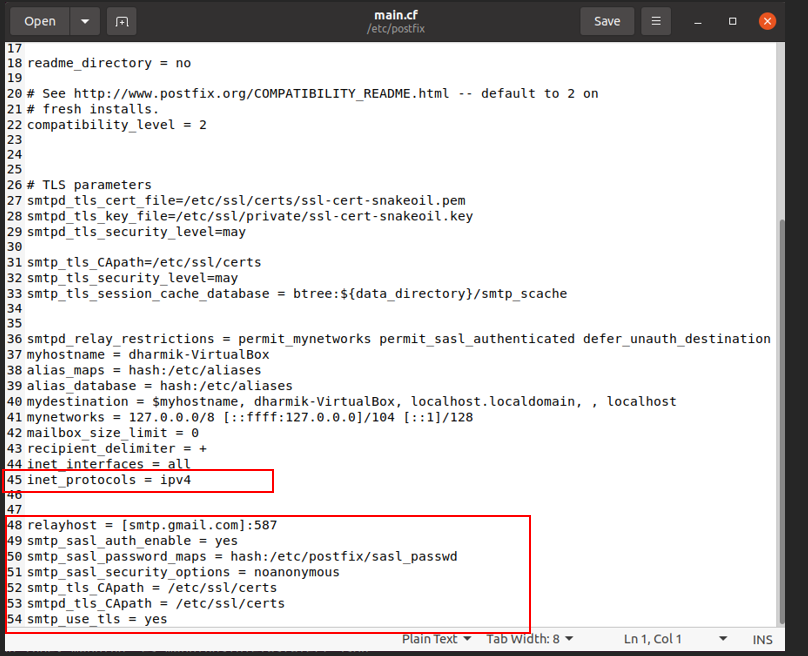
We now need to create a sasl_password file by typing the command:
Sudo gedit /etc/postfix/sasl_passwd
In the sasl_passwd file, type the following line of code:
[smtp.gmail.com]:587 [email protected]:qpdm abcd efgh ijkl
Note:
The email address is the email address you want the alerts to be sent to.
In order to use Gmail to send alerts, we need to enable two-factor authentication. Furthermore, we need to generate an App Password. The app password is the 12 characters seen above (abcd efgh ijkl)
We then run the following commands in the terminal.
sudo chmod 400 /etc/postfix/sasl_passwd
sudo postmap /etc/postfix/sasl_passwd
sudo systemctl restart postfix
This completes the setup of Elastalert and Postfix Gmail SMTP.
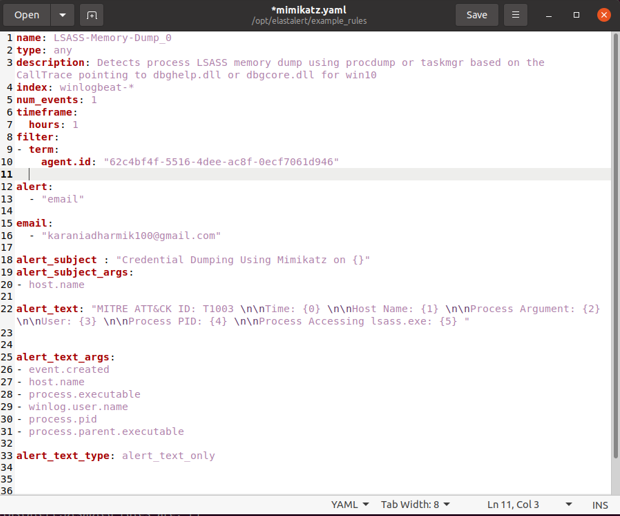
Creating the Mimikatz rule
I have created the following rule to detect Mimikatz and alert via email when it is run:
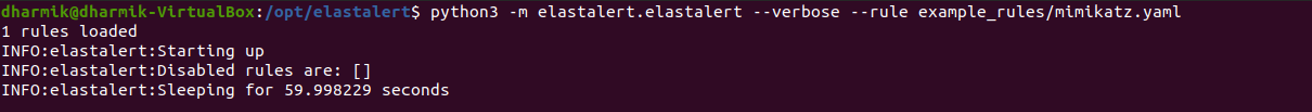
I save this and we can run Elastalert using the following command:
Python3 -m elastalert.elastalert –verbose –rule example_rules/Mimikatz.yaml
It runs as shown below:
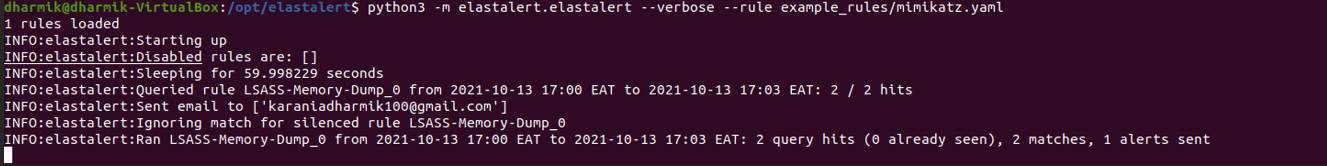
I then run Mimikatz on my Windows machine where I have configured winlogbeat. It detects and says “2 query hits … 1 alerts sent”.
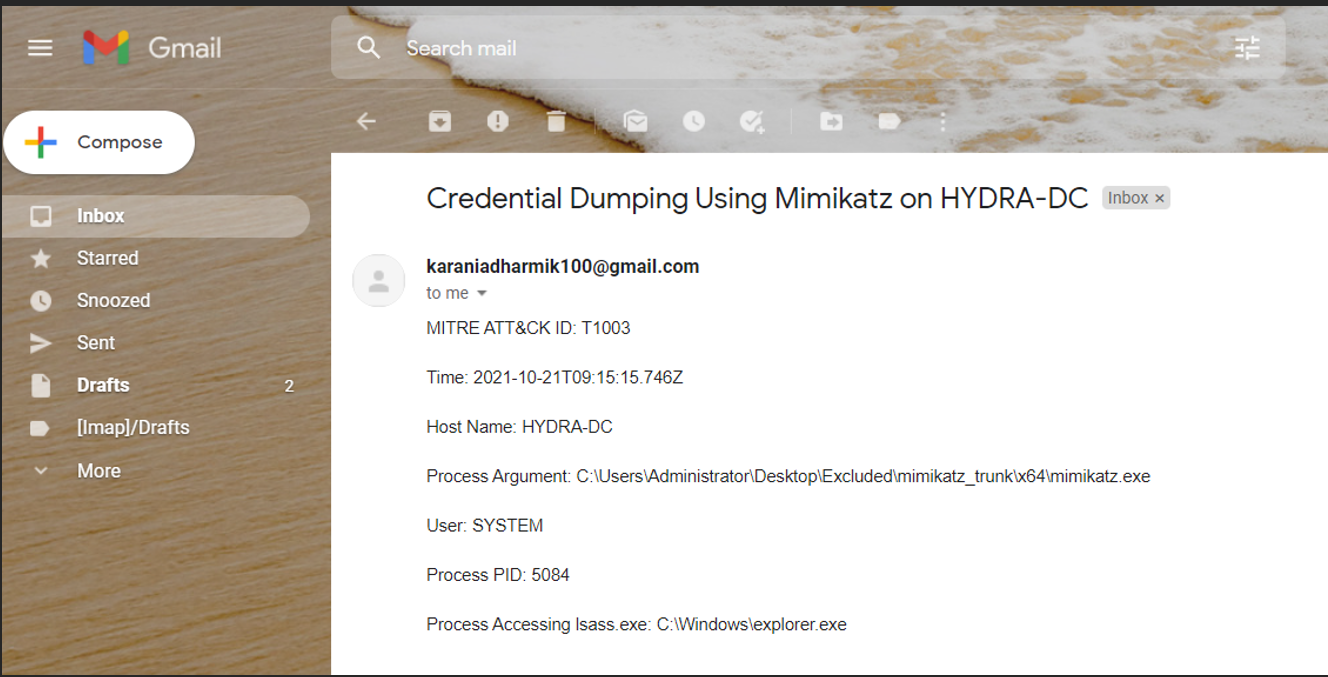
When I check my email, I receive the following alert.
References
https://www.hackingarticles.in/threat-hunting-log-monitoring-lab-setup-with-elk/
https://kifarunix.com/send-windows-logs-to-elastic-stack-using-winlogbeat-and-sysmon/
Disclaimer
The MacroSec blogs are solely for informational and educational purposes. Any actions and or activities related to the material contained within this website are solely your responsibility. The misuse of the information on this website can result in criminal charges brought against the persons in question. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.

![The Auror Project – Challenge 1 [Setting the lab up automatically]](https://macrosec.tech/wp-content/uploads/2022/04/Auror-Project-500x383.png)


