BLOG POSTS
Exploiting Insecure Deserialization Vulnerabilities Found in the Wild
EXPLOITIING INSECURE DESERALIZATION VULNERABILITIES FOUND IN THE WILD [...]
PDF Cracking With Cloud Computing
PDF CRACKING WITH CLOUD COMPUTING [...]
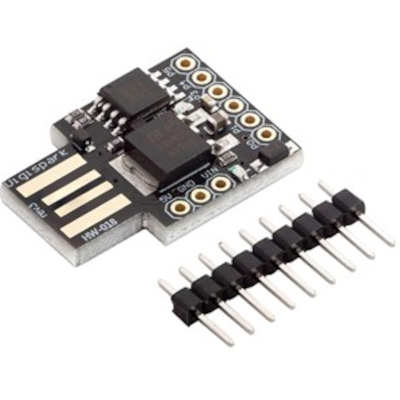
Creating BadUSB using ATTINY85
CREATING BADUSB USING ATTINY85 [...]
Linux Privilege Escalation Techniques using SUID
Linux Privilege Escalation Techniques via SUIDs [...]
HTTP Parameter Pollution (HPP)
HTTP Parameter Pollution (HPP) [...]
DNS Tunneling for Defense Evasion and Command and Control
DNS TUNNELING FOR DEFENCE EVASION AND COMMAND AND CONTROL [...]