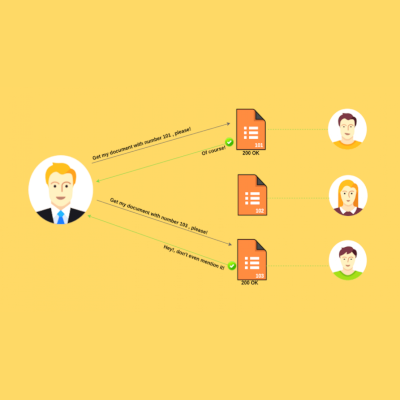
Posts related to red teaming.
DNS Tunneling for Defense Evasion and Command and Control
DNS TUNNELING FOR DEFENCE EVASION AND COMMAND AND CONTROL This blog post was written by Alex Maina. Introduction Before we look at exploiting DNS through DNS tunneling we need to understand DNS and how it is critical to an organization’s infrastructure. DNS is used to translate IP addresses into domain [...]